
MSP Guide to Harnessing AI for Threat Detection
Acting as a double-edged sword, Artificial Intelligence (AI) technology is now being used on both sides of the digital battlefield. On one end, cybersecurity practitioners leverage AI to improve cyber defenses. And on the other, threat actors use it to craft highly advanced malware and adversarial tactics. As stewards of their clients’ IT assets, MSPs need to understand how they can harness AI for their own cybersecurity engagements.
Traditional threat detection no longer cuts it
Traditional threat detection mechanisms primarily revolve around signature-based detection, which identifies threats by matching them against known malicious signatures in a database. While this method was effective in the past, it fails to detect new, unknown threats that have not yet been cataloged.
Additionally, today’s threats employ a variety of evasive techniques such as polymorphism, wherein malware alters its code to avoid signature-based detection, and living-off-the-land (LotL) tactics, wherein they use legitimate tools already present in the OS to carry out malicious activities. Because of the tools used, LOTL tactics are hard to distinguish from normal processes.
Some sophisticated threats even employ decoys to distract threat analysts and threat detection tools. For instance, in a sophisticated ransomware attack, perpetrators might launch a Distributed Denial-of-Service (DDoS) attack to divert the attention of the security team and then initiate the actual ransomware attack.
If you depend on traditional threat detection methods to monitor your clients’ IT environments, you won’t be able to keep up with these advanced threats. These sophisticated threats won’t match any known signatures or exhibit any easily recognizable patterns, thereby allowing them to persist in your clients’ environments for as long as they want.
So much to analyze in so little time
The urgency to detect threats early in the cyber kill chain can’t be overstated. The earlier a threat is identified, the quicker it can be eliminated or contained. This can prevent the threat from reaching its actions-on-objectives stage, whether that be data exfiltration, data encryption (in the case of ransomware), data destruction (in the case of wiper malware), or something more sinister. In turn, this will reduce the potential damage the attack may cause.
Unfortunately, manual methods of threat detection are inadequate for this task due to the sheer volume and speed of data that needs to be analyzed. Consider, for example, the daunting task of analyzing network traffic data. These are generated in the thousands, if not millions, every day and contain critical information about the activities happening on the network—malicious or otherwise.
Or think about the vast swathes of data produced by your endpoint devices. These devices produce a steady stream of information about processes, applications, and user behavior. Email traffic is another significant source of data that needs constant monitoring, as phishing remains one of the most common entry points for cyber threats.
Moreover, the increasing adoption of IoT devices and cloud services adds a new level of complexity to the data landscape. This influx of data is simply too vast and too fast for manual methods to effectively handle. In today’s cybersecurity battlefield, where every second counts, relying on manual methods is a sure way to expose your clients to a potential full-blown data breach.
AI can turn the tide in your favor
Artificial Intelligence has the remarkable ability to digest, understand, and analyze vast amounts of data in real-time, making it an invaluable tool in the battle against cyber threats. AI leverages machine learning algorithms to detect anomalies and patterns that might signify a cyber-attack, often identifying threats even before they detonate.
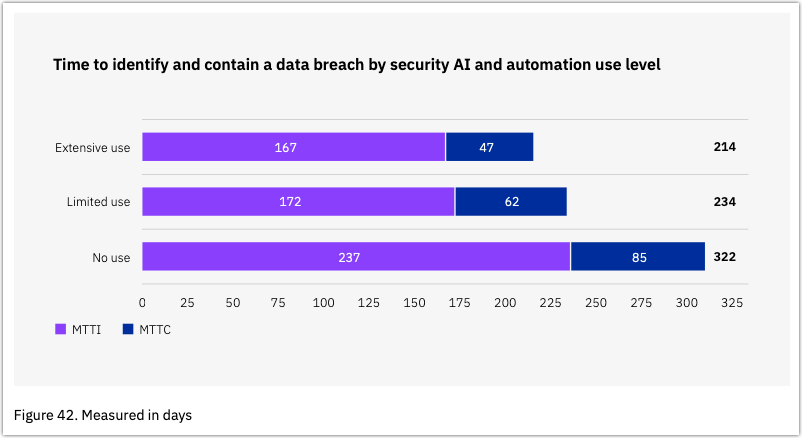
AI’s ability to detect and act on threats much faster isn’t just a theoretical concept. In the 2023 Cost of a Data Breach Report, extensive use of security AI and automation has been found to bring down the time it takes to identify and contain a breach to 66%. In the chart below, MTTI stands for mean time to identify, while MTTC stands for mean time to contain.
AI-powered threat detection systems, such as those offered by Intrusion, don’t just react to known threats like traditional security solutions. Instead, they proactively identify potential threats by comparing data from network traffic, endpoint devices, and other data sources against a continually updated knowledge base of threat indicators.
This rapid and dynamic approach allows for the detection of even the most sophisticated cyber threats, including advanced persistent threats (APTs) and zero-day exploits. When you leverage AI, you’ll have a better chance of keeping your clients’ environments threat-free.
Not only that, the integration of AI into your cybersecurity strategy will enable you to implement more efficient use of resources. With AI automating the labor-intensive process of threat analysis and detection, your security team can focus on strategic security planning and incident response. In a landscape where speed and efficiency can spell the difference between a successfully thwarted attack and a costly data breach, AI provides the edge you need to keep your clients safe.
So how exactly can you harness the power of AI for threat detection?
How MSPs can leverage AI for threat detection
Almost any cybersecurity solution requires a substantial investment. To secure a good ROI from your AI project, you may follow these four general steps.
1) Assess and define objectives
First and foremost, it’s crucial to evaluate your existing threat detection capabilities. This involves carrying out a comprehensive assessment of your current security infrastructure, processes, and skill sets. What tools are you currently using for threat detection? How effective have they been in identifying and neutralizing threats? Where are the gaps that leave your clients potentially exposed?
Once you’ve established a clear understanding of your current capabilities and identified any gaps, you can start defining clear objectives for your AI-driven threat detection. These objectives should align with both your organization’s and your clients’ security needs and may include goals like reducing the time required to detect threats, increasing the accuracy of threat detection, automating threat response, and/or improving the scalability of your threat detection capabilities.
You goals must be measurable. By establishing specific, measurable goals, you’ll be able to gauge the effectiveness of your AI-driven threat detection system and demonstrate its value to your clients later on.
2) Select a suitable AI technology
Choosing the right AI-powered threat detection solution is also crucial. You must look for a solution that’s suitable not only for your organization, but also for your clients’ unique environments and industries. Because each industry has its own assortment of cybersecurity threats and regulatory requirements, the solution must be adaptable and capable of meeting these specific needs.
As an MSP, you’re expected to have already taken the time to understand the needs of your clients, their existing security infrastructure, and the specific threats they face. Use that knowledge to select the most suitable AI solution.
Also, bear in mind that AI integration is not a one-time event, but a continuous process of learning and adapting to new and emerging threats. As such, the right AI solution should offer the flexibility to grow and evolve with your clients’ cybersecurity needs.
3) Integrate and deploy
Integrating your chosen AI solution into your clients’ existing security infrastructure requires careful planning and execution to ensure compatibility and minimal disruption. This is exactly why you shouldn’t take the previous steps for granted. A thorough assessment of your clients’ environments and careful selection of a suitable AI solution can greatly reduce complexity in integration and deployment.
During the integration process, maintain open lines of communication with all stakeholders. This will ensure that everyone is updated with the progress as well as any potential disruptions encountered along the way. As a best practice, plan for a phased rollout of the AI technology. This way, you can manage the changes more effectively and keep disruption to your clients’ operations to a minimum.
The AI solution should be chosen with interoperability in mind. It must be capable of working with different operating systems, platforms, and existing security applications. As much as possible, the AI solution should be able to seamlessly blend into the existing infrastructure without the need for extensive modifications.
Provide ample training to your clients and their staff. They should have a clear understanding of how the AI solution works, how to use it effectively, and what to do in case of any issues. The goal is not just to deploy the AI solution, but also to empower users to leverage it effectively.
4) Collaborate, evaluate, and adapt
Once your AI solution has already been successfully integrated and deployed, it’s important to maintain constant communication with your clients. Regular updates regarding system performance and any changes in the threat landscape are essential in ensuring project success as well as in trust-building.
As with regards to system performance, it’s important to continuously monitor and evaluate the efficiency of the AI solution post-deployment. Regular performance assessments provide insights into how well the AI solution is detecting, diagnosing, and neutralizing threats. They also highlight areas where the AI may need enhanced training or updates.
Remember, the threat landscape is not static. Cyber threats constantly evolve. They always become more sophisticated and harder to detect. It’s crucial to make sure your AI solution is capable of adapting to these evolving threats.
Lastly, keep an open mind when it comes to new client requirements. As their businesses grow and evolve, their security requirements will change. Regularly consult with your clients to understand their changing needs, and work towards adapting the AI system to meet those needs. This will help keep the AI solution relevant and effective, making it a worthy investment for your clients.
By following these four general steps, you can efficiently harness AI for effective threat detection and, in turn, provide enhanced cybersecurity services to your clients.
Intrusion – a cybersecurity solution that uses AI for threat detection
Here at Intrusion, we continue to witness how AI dramatically boosts threat detection time and time again. AI works best when it learns from massive volumes of relevant data. Intrusion has one of the—if not the—largest collection of reputation and historical data of the Internet’s IP addresses and hostnames. By continuously learning from this ever increasing collection, Intrusion is able to adapt to ever-evolving threats, ensuring that it’s never a step behind.
Intrusion operates in a zero-trust manner, evaluating all inbound and outbound connections with the assumption that all networks have been compromised. When a threat is detected, it’s automatically blocked.
As a network-based solution, Intrusion has a significant edge over host-based systems in terms of compatibility. Since it’s deployed directly into your network, rather than on individual devices, you won’t have to worry about any compatibility issues. Plus, you get the benefit of a broader view of your entire network, something that would be impossible with a host-based solution.
Intrigued? We’d love to chat more about how Intrusion can fortify your network security. Get in touch with us and let’s discuss how AI can give you the upper hand in your own cyber battles.


