Why Intrusion
See the unseen. Know the unknown.

To fully secure your network,
you need to see everything.
Our Global Threat Engine powers everything we do.
It’s a Zero Trust world.
Here’s why you can trust us.
We’ve been networking, threat hunting, and analyzing network behavior for over 30 years. Our network intelligence analysts know what to look for.
Networking
Threat Hunting
Analyzing
Lower complexity. Heighten security.
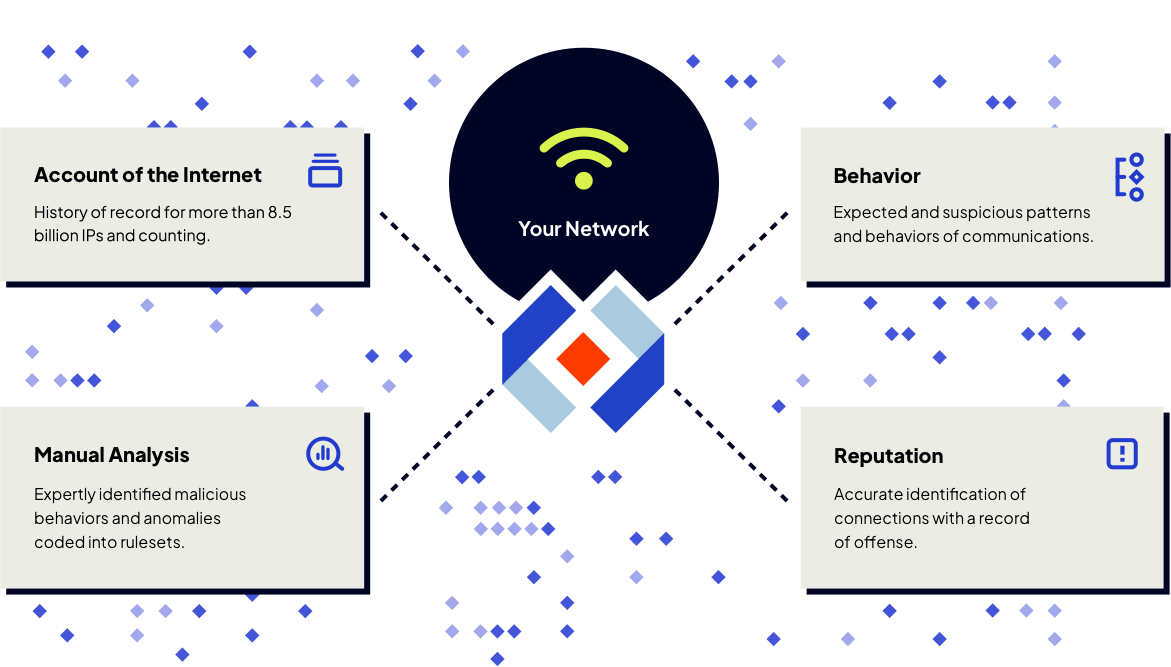
We vet every connection on your network
Cybersecurity systems are only as intelligent as their data. Intrusion’s Threat Engine is our proprietary database with historical records for every known registered IP and hostname paired with related behavior and reputation intelligence.
- Proprietary global database (no sifting through data feeds, multiple, sources, or crowdsourced intelligence)
- Hybrid of reputation, behavior and historical data

Decrease network vulnerabilities
See malware your other security products were not aware of. Intrusion enhances your current security stack and hardens your Zero Trust strategy.

Zero Trust mindset
Intrusion operates under the assumption that all networks have been compromised. There is no inherent trust. We evaluate all inbound and outbound connections to prevent deployment of Zero-Days that may exist in your environment.
Protected by Intrusion




Get the Global Threat Engine
working for you.
On-Premise
Network Protection
Install Shield behind your firewall to protect your network from malicious inbound and outbound traffic.
Cloud Network Security
Protect your cloud environment with an automated protective gateway.
Endpoint Protection
Enable secure access of company resources from any device, anywhere in the world.
Cyber Threat
Consulting
Get in-depth network analysis, threat intelligence reporting, and strategic guidance.
Compliance and Certifications
HIPAA
Compliance with the U.S. Health Insurance Portability and Accountability Act (HIPAA) requires companies that work with protected health information (PHI) to implement and follow physical, network, and process security measures.
Intrusion abides by these standards and is HIPAA compliant.
SOC 2
SOC 2 is a voluntary cybersecurity compliance framework developed by the American Institute of CPAs (AICPA) for service organizations that specifies how organizations should handle customer data.
Intrusion’s SOC 2 Type 2 compliance has been verified and confirmed by Prescient Assurance in accordance with the AICPA’s Trust Service Criteria for Security.
GDPR
The General Data Protection Regulation (GDPR) provides a legal framework for keeping everyone’s personal data safe by requiring companies to have robust processes in place for handling and storing personal information.
Intrusion abides by all rules and regulations for personal data and is GDPR compliant.
Trust is everything to us.
