ENDPOINT PROTECTION
Centralized cybersecurity
for a distributed workforce.
Enable secure, remote access of company resources from any device, anywhere in the world.

More devices mean more exposure.
When everything happens on-premise, your cybersecurity perimeter is clearly defined. Not so in today’s hybrid work environment. Remote workers, mobile devices, cloud devices, and separate network enclaves all expand the perimeter – and the attack surface. Without endpoint protection, your security layer is stretched dangerously thin.
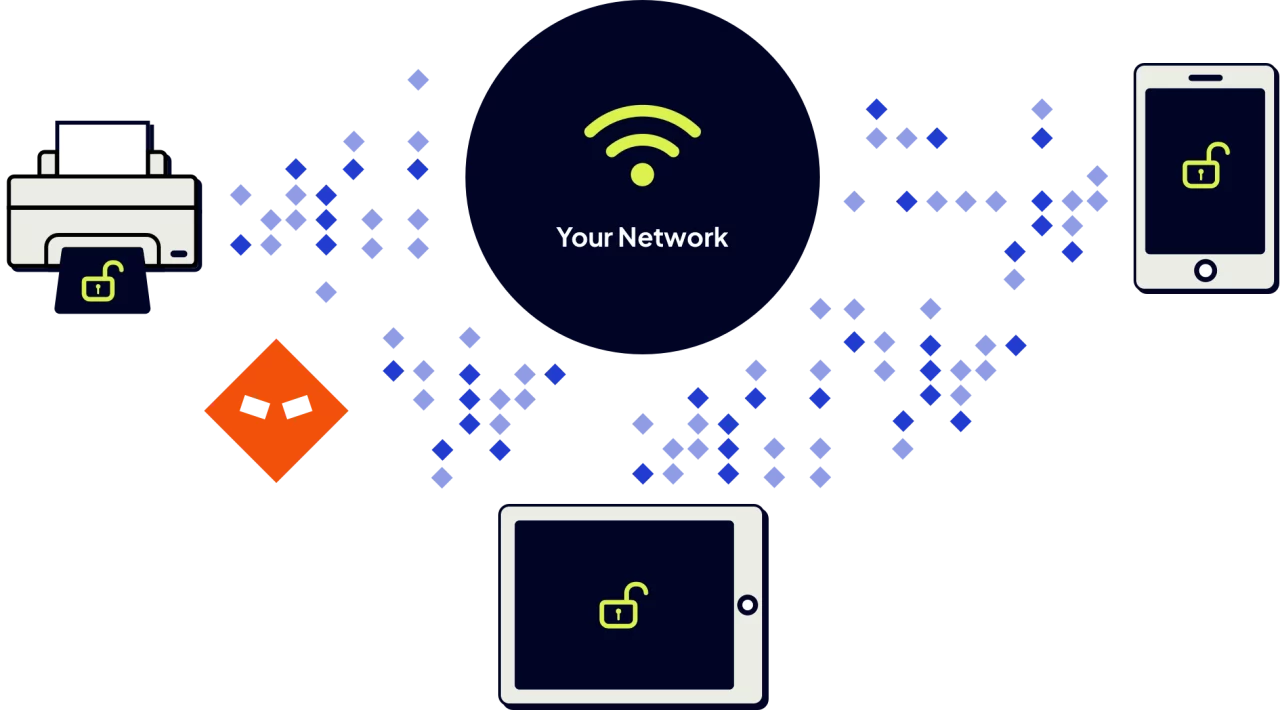
Harden your expanded network surface with Shield Endpoint.
Enable remote connectivity and safe web browsing between secure network enclaves. Shield Endpoint allows you to manage Bring Your Own Device (BYOD) policies with confidence knowing that authorized device connections are known, monitored, and protected.
Enable safe
remote work
Automatically redirect
malicious sites
Strengthen your Zero
Trust network
No device unsecured. No connection unnoticed.
Know the good
from the bad.
Get real-time inspection of inbound and outbound connections. Shield Endpoint leverages the Intrusion Global Threat Engine’s historical knowledge of trillions of domains and IPs to instantly identify and block malicious or unknown connections from any device.

Gain peace of mind with triple authentication.
Shield Endpoint uses a peer-to-peer (P2P) encrypted network overlay that allows users to securely access defined network endpoints via an approved physical device, Zero Trust credentials, and security certificate.

Enable safe web browsing.
When a browsing request for a suspicious or malicious website is detected, a built-in browser plugin (Shield Renderer) transparently redirects users to a safe, cloud-based browsing environment. Users can scroll, follow links, submit forms, and view content normally without introducing risk to the browsing device or your network.