
Why You Need to Monitor and Control Outbound Traffic
Traditional cybersecurity strategies usually operate under the assumption that threats originate from outside the corporate firewall. That’s why we typically focus on restricting inbound traffic when we set firewall rules. This approach leaves out a wide range of threats that might already be inside your network, but have to perform outbound communications before they can compromise your systems.
In this post, we’ll discuss:
- The importance of monitoring and controlling outbound traffic
- Threat activity that relies on outbound communications
- Insecure practices that result in vulnerable outbound connections
- Compliance implications of monitoring and controlling outbound traffic
- Challenges of restricting outbound traffic
- A practical solution for carrying out those restrictions
Importance of Monitoring and Controlling Outbound Traffic
There is a straightforward reason why you need to monitor and control outbound traffic. Whenever you have outbound traffic that has the potential to cause harm to your organization, it means the threat is already inside. It’s probably just a step away from inflicting harm.
So, unless you can block that malicious outbound traffic, your IT infrastructure, digital assets, and, consequently, your business operations could be in imminent danger. If that threat establishes that outbound connection, your organization could be at risk of a data breach, a ransomware outbreak, getting ensnared in a botnet, and so on.
Before we discuss how to mitigate these threats, let’s first familiarize ourselves with some of the most common threats that perform outbound communications.
Malware Calling Home
In many cyber attacks, a malware infection is just one of the initial stages of a more extensive operation. Some of these malware still have to communicate with a Command and Control (C&C) server in what are known as call-home activities. The Microsoft Digital Defense Report 2024 identifies attack C&C infrastructure among the enablers of ecosystem threats. Malware conduct call-home activities to accomplish various tasks such as:
- Establishing a connection with the C&C server. It’s also one way of informing malware operators that it (the malware) has successfully established a beachhead in the target system;
- Obtaining updates from the C&C;
- Requesting commands from the C&C; and
- Exfiltrating stolen data to the C&C.
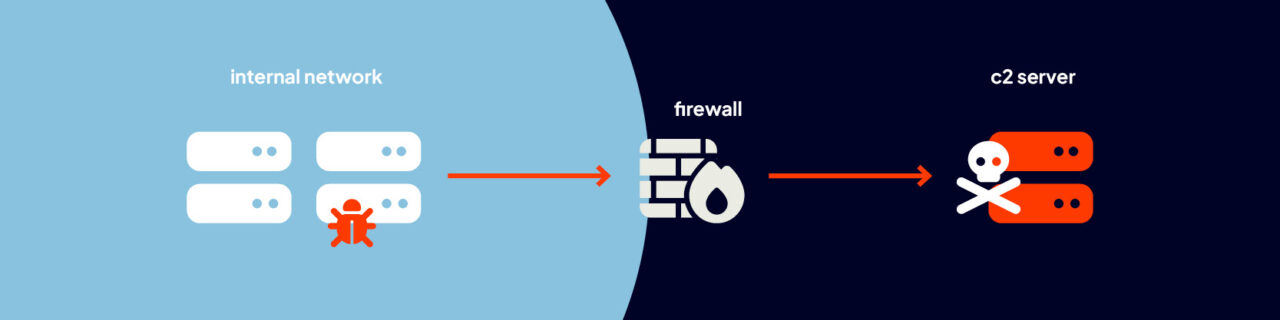
Certain types of ransomware, botnets, and cryptomining/cryptojacking malware are some of the cyber threats that perform call-home activities.
Not all harmful outbound connections come from malware, though. Some of them are initiated by unwitting users.
Insecure User Practices That Expose Them to Malicious Sites
Many users find it hard to identify malicious content. It’s the reason why some easily fall for social engineering attacks like phishing. According to the Comcast Business 2024 Cybersecurity Threat Report, phishing is the primary method threat actors use to gain initial network access. Moreover, the same report says that over 90% of the phishing attacks Comcast Business successfully blocked would have directed users to sites hosting malware.
Basically, when a user clicks a link on a phishing email, the ensuing outbound request may end up on a server that hosts malicious software. In the Sophos State of Ransomware Report 2024, 34% of respondents identified email-based approaches as the root cause of ransomware attacks.
Malware downloads can also happen when users browse the web and then unwittingly click on links that lead to sites serving malware. Since all these user-initiated actions are outbound connections, they’re not blocked by firewalls using default inbound-restricting rules even if the connections lead to malicious sites.
Data protection authorities are aware of these threats. Some of them have even incorporated risk-mitigating measures into regulatory mandates.
Compliance Requirements Involving Outbound Traffic
Requirement 1.3.2 of the Payment Card Industry Data Security Standard (PCI DSS) v 4.0.1, for example, calls for restrictions on outbound traffic originating from the cardholder data environment (CDE). As per Requirement 1.3.2, only outbound traffic that is deemed necessary should be allowed. All other outbound traffic must be blocked.
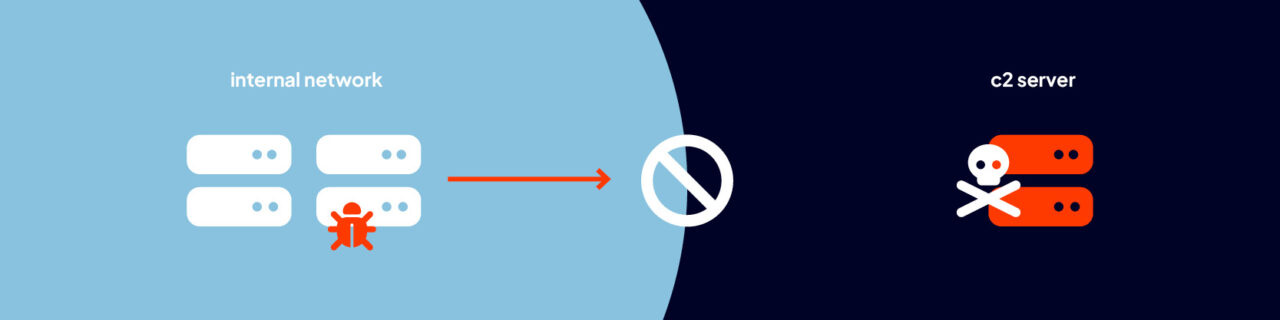
Corresponding guidance in the PCI DSS Requirements and Testing Procedures document offers the following reason for this requirement:
Requirement 1.3.2 “aims to prevent malicious individuals and compromised system components within the entity’s network from communicating with an untrusted external host.”
That explanation corroborates our earlier discussion.
Challenges in Restricting Outbound Traffic
While you’re already aware of the threats involving outbound traffic, imposing restrictions on these traffic types isn’t easy. For one, many legitimate applications have to initiate connections to external services. File transfer clients, email clients, web browsers, remote desktop clients, update tools, and others must make outbound connections to perform business-related functions.
To avoid detection, some malware varieties use well-known protocols like FTP, HTTP, HTTPS, and SMTP to communicate with their C&Cs. Businesses usually employ these protocols in legitimate business processes. Hence, security solutions typically allow them to pass through. Some botnet-infected machines, for instance, retrieve commands from their C&Cs using HTTP requests.
If you’re unfamiliar with network protocols, HTTP is a protocol web browsers use to connect to a website. For this reason, IT admins usually configure firewalls to allow HTTP to pass through. Thus, you can’t just block all outbound traffic or block based on protocol. There has to be a better way.
A More Effective Solution To Restricting Outbound Traffic
Although it can be challenging to distinguish outbound traffic caused by malware from that coming from legitimate applications and processes, a couple of tactics still work.
One way is to analyze how outbound communications are carried out. You can look for specific patterns and behavior associated with malware and other threat actors. Another way is to determine the reputation of the destination IP address of the outbound traffic. More often than not, threat actors connect to IP addresses with bad reputations.
Of course, traditional firewalls have no way of employing these methods. You need an advanced security solution that has these capabilities. Intrusion Shield combines pattern and behavior-based techniques with reputation-based threat detection.
Intrusion uses one of the largest threat intelligence databases, with decades of historical data on billions of IPs, hostnames, and domains. If a malware, or potentially even a zero-day threat attempts to connect to its C&C, Intrusion blocks the malicious connection attempt. Have questions? Book a quick meeting now.



