
5 Effective Countermeasures Against Zero-Day Attacks
How do you secure a weakness in your IT infrastructure if you don’t know it exists? That’s the kind of problem organizations face when dealing with zero-day vulnerabilities and corresponding zero-day attacks. However, difficult as it may sound, there are actually ways to mitigate the risk of a zero-day attack. We’ll talk about those in detail in the following sections.
Before we do that though, let’s have a quick review of what a zero-day (a.k.a. 0-day) is and why it’s so difficult to stop.
What’s a Zero-Day Attack Again?
For those who aren’t familiar with the term or haven’t fully understood what it means, a “zero-day vulnerability” is a vulnerability—usually in the form of a software bug—that’s only been recently discovered and has just started making the rounds in cybercrime circles. The cybersecurity community may or may not have heard about it yet, but what’s certain is that a fix or patch for that vulnerability hasn’t been developed, let alone released, yet.
This gap gives threat actors a window of opportunity to build an exploit for that vulnerability and carry out an attack on systems in which that vulnerability exists before a patch is released. This attack, which takes advantage of a zero-day vulnerability, is known as a “zero-day attack”. Used alone, the term “zero-day” or “0-day” may refer to either the vulnerability or the attack, depending on the context it’s being used.
Since the cybersecurity community will have no prior knowledge about the nature of a particular zero-day threat, antimalware vendors as well as other security solutions (e.g., intrusion detection/prevention systems) vendors will not have assigned a signature to it. A “signature” is simply a representation that uniquely identifies that particular threat and is used by signature-based security solutions, like certain antivirus and IDS/IPS solutions, to detect that particular threat.
So, if your installation of the software in question is still unpatched for that zero-day vulnerability and your security solutions are unable to detect the vulnerability’s corresponding zero-day exploit, does that mean you have no choice but to be a sitting duck? Not really. There are some solutions you can put into action.
Subscribe to Threat Intelligence Feeds
Threat intelligence (TI) feeds are streams of data about cyber threats. A typical threat intelligence feed may contain information about:
- Recent cyber attacks;
- Emerging threats;
- Exploitation techniques;
- Indicators of compromise (IOC) such as IP addresses, domains, malware hashes, etc.;
- And, yes, newly discovered vulnerabilities.
Some feeds are paid, while some are free. Should you wish to check out some free sources, try the US Cybersecurity & Infrastructure Security Agency (CISA), SANS Internet Storm Center, and SecLists.Org. You can obtain the feeds through RSS, online bulletins, information sharing communities, and even Twitter. Once you’ve collected data from threat intelligence feeds, you can factor them into your security policies, tool settings, operations, and awareness training to mitigate the risk of a zero day attack.
Security alerts at CISA.gov
In the case of TI about a 0-day vulnerability that affects one of your applications, you’ll want to ask your software vendor if they’re already working on a patch and when it will be made available. This might not protect you from an imminent or ongoing 0-day attack, but applying a patch as soon as it’s available does reduce an attacker’s window of opportunity to exploit that vulnerability.
Do bear in mind that data provided by some of these feeds still have to be analyzed and applied by an infosec expert before they can make practical sense to your organization. TI feeds are useful if you have the in-house talent to act on the information they deliver. Otherwise, the feeds can only be a source of distraction and alert fatigue.
Conduct Security Awareness Trainings
Before a zero-day attack can exploit a vulnerability in your system, the attacker will have to somehow gain an initial foothold into your network. According to the 2022 Cost of a Data Breach Report, the top 5 most commonly used initial attack vectors as of last year were the following:
- Stolen or compromised credentials
- Phishing
- Cloud misconfigurations
- Vulnerability in third-party software
- Malicious insiders
Out of those five attack vectors, four of them (#1, #2, #3 and #5) take advantage of or involve end users. Therefore, one way to defend your organization against these initial attack vectors (and in turn, 0-day attacks) is to improve your end users’ security awareness.
Train your users how to distinguish a phishing email from a legitimate one. Teach them cloud configuration best practices. Educate them about the risks of insecure password practices and how to mitigate them. The goal is to make your users more appreciative of cybersecurity and to nurture a cybersecurity culture throughout your organization.
Once your users develop heightened security awareness, they won’t easily fall for a social engineering attack. They won’t nonchalantly click any download link or share their credentials to an alleged “tech support staff”. They’ll be more conscious when setting up cloud resources. And so on and so forth.
Although security awareness training can certainly improve your organization’s overall security posture, don’t be overly dependent on it. For most users, the main objective is to get the job done. If it entails circumventing a security policy or skipping a more secure step, some will sadly take that route.
Institute Regular Threat Hunting Activities
Threat hunting is a cybersecurity practice wherein you start with a mindset that a threat might have already infiltrated your defenses and then proactively search for that threat. It differs from the normally reactive nature of security operations wherein you respond to security alerts. Threat hunting is meant to uncover highly evasive threats that might have avoided your threat detection tools.
You usually conduct threat hunting in conjunction with threat intelligence. Basically, you would use TI data such as logs, IOCs, information about recent cyber attacks, as well as established threat actor tactics, techniques, and procedures (TTPs) to enrich threat hunting tasks.
While threat hunting activities are primarily designed to search for existing threats in your network, you may also come across previously unknown vulnerabilities (including 0-days) and other weaknesses along the way. You may even chance upon insecure employee behavior such as the use of weak passwords, shadow IT, rogue devices, and unencrypted sensitive data.
Moreover, even if threat hunting isn’t meant to prevent threats from reaching your network, it can still reduce dwell time. In the context of cybersecurity, dwell time is the time between the initial compromise to the point where the threat in question is uncovered. To minimize a zero-day attack’s impact to your business, you want its dwell time to be as short as possible. Threat hunting can help in that regard.
Cybercrime organizations never stop looking for zero-day vulnerabilities to exploit. As such, you should also conduct threat hunting on a regular basis to improve your chances of finding threats if any of those exploits happen in your own backyard.
Monitor and Control Outbound Traffic
As intimated earlier, security tools like certain firewalls as well as intrusion detection/prevention systems (IDPS) that depend purely on threat signatures are incapable of detecting 0-day attacks. While you can employ threat hunting to uncover an ongoing attack, not many organizations have the in-house talent to do that.
There are a few workarounds. You can narrow down your “threat hunting” activities to certain IOCs that are associated with most threats. You may not catch them all, but if you can snag the majority of the threats that are out there, that should already boost your threat mitigation initiatives, right? One example of such IOCs is outbound traffic that connects to a malicious host.
Many threat TTPs involve outbound traffic. In the case of malware, for instance, they use it for various call-home activities such as:
- Establishing a connection to the C2 server
- Obtaining updates from their C2
- Requesting commands from their C2
- Exfiltrating stolen data to their C2
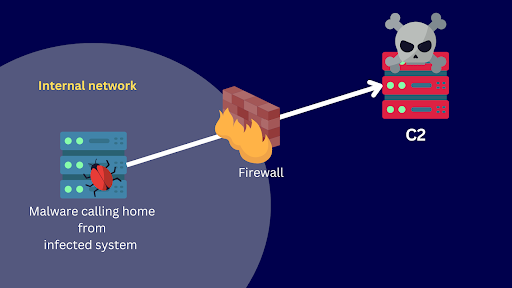
Call-home activities are so deeply ingrained among threat actors, even zero-day threats use them. So if you can somehow monitor outbound traffic and block those that lead to known malicious IP addresses, you can stop an ongoing zero-day attack.
We have a more detailed discussion on this type of threat activity as well as a recommended solution that acts on it in our blog post “Why You Need to Monitor and Control Outbound Traffic.”
Implement Applied Threat Intelligence (ATI)
Threat intelligence is a key ingredient to defending your network against a zero-day attack, but it’s just half of a complete solution. As indicated earlier, you still need to analyze and process TI data and then incorporate it into your other cybersecurity processes like threat detection and threat hunting before you can obtain its value. Therein lies the problem.
The job of analyzing, processing, and utilizing TI data is not exactly a walk in the park. You need a threat analyst or, if you have a massive collection of data, a team of threat analysts to do all that for you. There is however an emerging class of solutions that incorporates the entire process (collecting, analyzing, processing, and utilizing TI data) in one single solution. It’s called applied threat intelligence (ATI).
In its most basic form, a typical ATI solution will continuously collect all relevant TI data and automatically use it to stop a cyber attack in its tracks. As the name implies, ATI immediately puts threat intelligence to use. You don’t have to hire a threat analyst to do all those tasks we mentioned earlier.
An ATI solution like Intrusion combines historical account of the network, an up-to-date database of reputation data, a continuous assessment of network behavior, and expert analysis to detect and terminate threat activity without requiring any threat signature. Yes, that means, ATI can stop zero-day threats as well.
Final Thoughts
Zero-day attacks are highly sophisticated threats that can’t be averted using traditional threat detection-based tools. In this post, we talked about some of the solutions you can employ to significantly mitigate the risk of these types of attacks.
That said, you need to understand that some of the most effective countermeasures like threat intelligence and threat hunting require a great deal of time and an advanced level of expertise. If you’re running a small or medium-sized business (SMB), chances are you don’t have the capability in-house.
Fortunately, there are ways to overcome those limitations. Contact us and we’ll find a strategy that best fits your organization.


