
How to Block Data Exfiltration Before It Becomes a Full-Blown Breach
The ultimate objective and often last stage of most cyber attacks – data exfiltration – can lead to a costly, reputation-damaging data breach. In this post, we’ll tell you how you can potentially prevent or stop data exfiltration in its tracks and prevent sensitive data from falling into the hands of cybercriminals.
Before that though, let’s get on the same page about what it is and why it’s so critical to stop.
What is Data Exfiltration?
In the context of cybersecurity, data exfiltration is the process of covertly transferring stolen data from a victim’s system (e.g., a server, PC, laptop, etc.) to an attacker’s system. The exfiltrated data usually involves:
- Personally identifiable information (PII)
- Patient medical information
- Debit/credit card data
- Login credentials (usernames/passwords)
- Financial data
- Intellectual property
- Or any type of data of value to the attacker and yourself
Most of these data types can be sold to identity thieves and other cyber criminals in the Dark Web. In the case of financial data and intellectual property, they can be offered to your competitors—if a competitor isn’t responsible for the hack in the first place.
Although data exfiltration can be carried out manually by an individual—e.g., by a threat actor that transfers data from a compromised PC to a USB stick—it’s usually initiated by malware. In this case, the malware typically uploads stolen data to an external system like an attacker’s command-and-control (C2) server. As soon as the exfiltration completes, it’s game over.
How Crucial Is It To Block A Data Exfiltration Event?
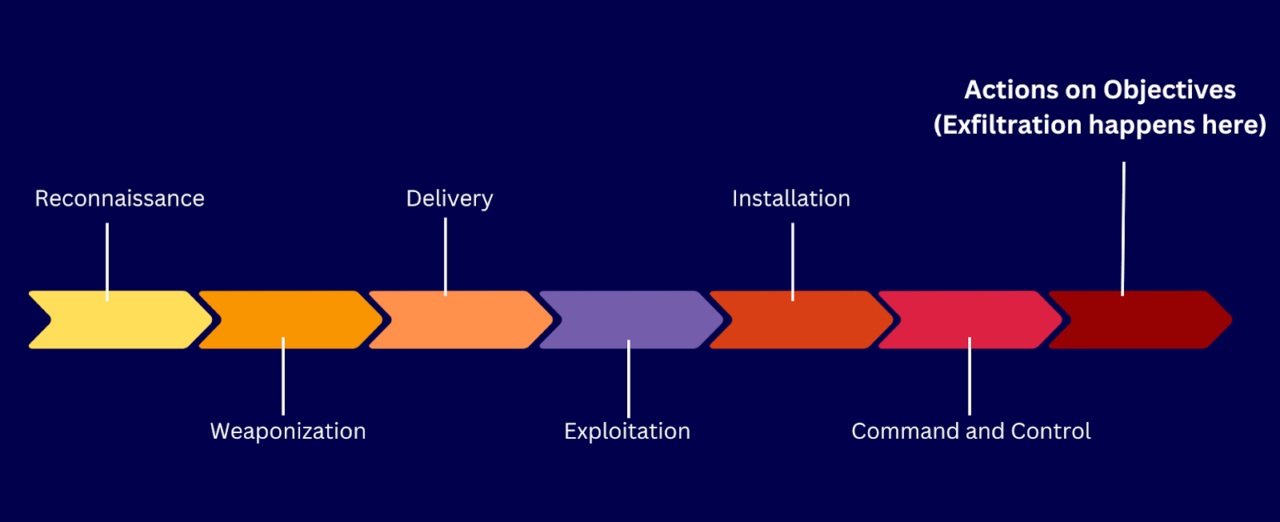
Data exfiltration is usually the last stage of the cyber kill chain. In many cases, it’s an attacker’s ultimate goal when it sets out to infiltrate your network. Once the data exfiltration activity completes, you’ll have a costly data breach incident in your hands. Just how expensive can a publicly disclosed data breach be?
When you take into account the requisite post-data breach activities such as digital forensics, crisis management, audit and assessment, breach notification, as well as the cost of credit monitoring, identity protection services, regulatory fines, legal expenditures, and so on, and add to that the cost of customer churn, reputation damage, and loss of business, the total cost can run up to millions of dollars.
As of last year, the average cost of a data breach reached USD 4.35 million. If you’re in the United States, the costs are going to be much higher. The average cost here is $9.4M. And if you’re in certain industries like Healthcare, costs can go over $10M.
Your problems can get even worse if the attacker happens to be a ransomware operator. Many ransomware campaigns now follow a double extortion business model. Before encrypting your data, some ransomware operators will exfiltrate copies of that data first. So, not only will you be unable to access your data, you’ll also run the risk of having your stolen data disclosed to the public if you don’t pay the ransom.
The consequences of allowing a data exfiltration event to run its course can be very costly. So if you can prevent exfiltration from happening or at least abort it, you can save yourself a lot of pain.
How to Block Data Exfiltration
Network-based data exfiltration techniques usually employ commonly used protocols like DNS and HTTP, which are normally allowed by traditional security solutions like firewalls. For example, threat actors may encode stolen data in DNS queries. Since protocols like DNS and HTTP are considered harmless, they’re rarely ever inspected, let alone blocked.
However, regardless of the technique used, most malware-based data exfiltration activities involve outbound connections to that malware’s C2 server. If you can somehow detect these outbound connections, it should be trivial to block them at your firewall or intrusion detection/prevention system (IDPS).
Sounds like a plan. But how do you determine if an outbound connection is directed at a C2 server or any malicious server for that matter? One way is to find a reliable source of cyber threat intelligence (CTI) data that identifies certain Indicators of Compromise (IoCs) such as known malicious IP addresses. You can then plug the threat intelligence information into your firewall or IDPS, which will then carry out the detection and blocking for you. We’ll share an easier way shortly.
As we discussed earlier, exfiltration is already a late-stage event. Once an attacker reaches that point, you’ll have very little wiggle room to prevent your data from reaching the dark web. So, ideally, you’ll want to stop data exfiltration before it even begins. Is that even possible?
Is It Possible To Prevent Data Exfiltration?
If you recall, data exfiltration is preceded by six other steps in the cyber kill chain. You can therefore stop the kill chain from reaching Actions on Objectives (ergo, exfiltration) by focusing your threat protection initiatives on these earlier stages.
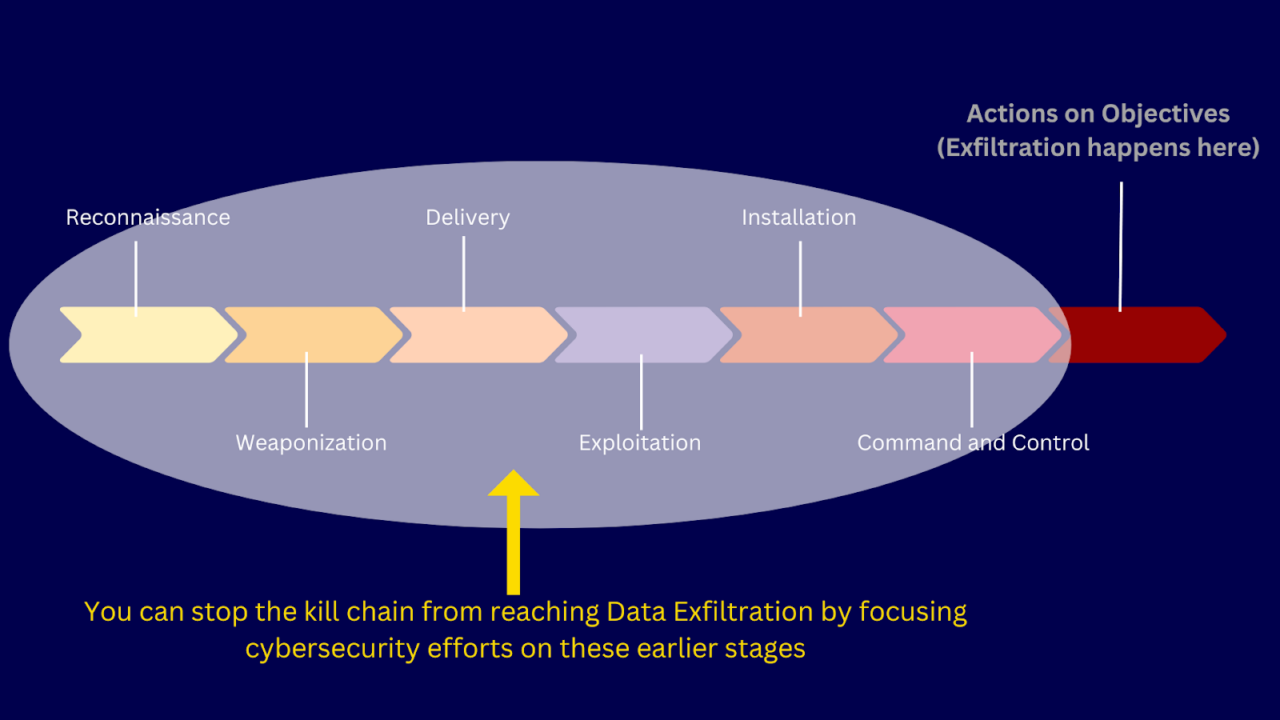
Any malware that performs network-based data exfiltration carries out multiple outbound communications with their C2 prior to data exfiltration. Known as C2 call-home activities, these outbound communications are carried out by malware to:
- Confirm that it (the malware) has already infected the target system and is ready to accept commands
- Retrieve updates
- Request commands
Again, if you can detect these outbound connections and block them, the malware can’t acquire the capabilities to perform Actions and Objectives. For example, it won’t be able to receive the commands and other payloads to perform other necessary threat activities like lateral movement and privilege escalation.
You see, upon gaining initial access to your network, most malware won’t be fortunate enough to land on the system where they’re supposed to exfiltrate data. Thus, to reach their ultimate destination, they still have to perform additional threat activities like lateral movement and privilege escalation. You can prevent those activities from ever taking place by blocking communications to their C2.
So what happens to a malware that fails to connect with its C2? It will just lay there incapacitated until you find and remove it. If you managed to block those malicious connections, you’ll know that a threat is inside your system. You can then conduct a threat hunt to search and destroy the threat in question. If you don’t know how to do that, you can hire reputable cyber threat hunters to do the job for you.
Time is crucial, so it’s important to automatically block a data exfiltration event as well as any other call-home activity as soon as it happens. But you can only execute that properly if your threat intelligence, detection, and prevention solutions are in-sync.
Preventing Data Exfiltration Through Intrusion
Not all organizations have the capability to do CTI—i.e., collect, enrich, and analyze threat intelligence data—let alone utilize the processed information in their threat detection tools. Intrusion takes care of all these steps with one security tool.
Intrusion combines its extensive historical records of every known registered IP and hostname with behavior and reputation intelligence to detect AND automatically block network-based threat actions such as data exfiltration and other C2 call-home activities.
Intrusion’s Global Threat Engine can determine if a host on the Internet is malicious or not. It can also identify suspicious network behavior. By leveraging Intrusion’s ability to detect threats at multiple points in the cyber kill chain, you can significantly reduce the risk of a data breach and avoid the costs associated with it.
You probably want to know if Intrusion is right for your business. We can help you with that. Let’s talk.


