
Top 5 Remote Work Cyber Threats
While lockdowns are fast becoming a distant memory, one of the major by-products of them remain. Remote work has now become an integral component of almost every business environment. And like everything else, the threats have come with it.
Remote work was already on the rise before the COVID-19 pandemic and then surged as businesses scrambled to remain operational despite the lockdowns. Although the number of remote workers have since gone down, it’s still considerably high.

According to Deloitte’s 2022 Connectivity and Mobile Trends report, 45% of survey respondents said at least one member of their household was working under a hybrid setup, i.e., part of the time working from home and part of the time from the office. The same report further stated that 75% of employees with remote work experience are now more inclined to choose remote or hybrid work options.
Impact of remote work on your cybersecurity posture
While remote work practices improve employee productivity, flexibility, and satisfaction, they also tend to undermine cybersecurity controls. When you have employees working outside your corporate firewall, the protection afforded by that firewall to those employees when they are inside your network ceases.
When that happens, those employees become more exposed to cyber threats. And since remote workers are normally outside the purview of their company’s security defenses, they’re more vulnerable. In the 2022 Cost of a Data Breach, researchers reported that costs for data breaches where remote working was a factor in causing the breach were higher by about USD 1 million than breaches were remote working wasn’t a factor.
There are number of cyber threats facing remote workers, but for this year, you should pay most attention to the following:
1. Phishing attacks
Researchers working on Microsoft Digital Defense Report 2022 said they “continue to observe a steady year-over-year increase in phishing emails” and that “The shift to remote work … saw a substantial increase in phishing attacks aiming to capitalize on the changing work environment”. This observation aligns with data from the Anti-Phishing Working Group (APWG), which shows that for 5 consecutive quarters now, phishing attacks have been on an uptrend and breaking previous records.
Note: Read the phishing uptrend in more detail in our post about endpoint security threats.
While the Microsoft and APWG reports don’t distinguish between phishing attacks on different types of devices (i.e., desktop and mobile), it’s worth noting that phishing attacks on mobile devices, as discussed in our recent blog post on mobile threats, are harder to identify due to various factors related to the limited screen real estate of these devices.
2. Credential stuffing
Credential stuffing is an attack that takes advantage of the common end user practice of reusing the same login credentials across multiple systems, applications, and cloud services. When users reuse passwords, login credentials stolen from a previous hack on one site (e.g., at Yahoo, Facebook or Twitter) can be used in a credential stuffing attack on other sites like say an online banking site, an e-commerce site, your company portal, your file transfer service, your VPN service, and so on.
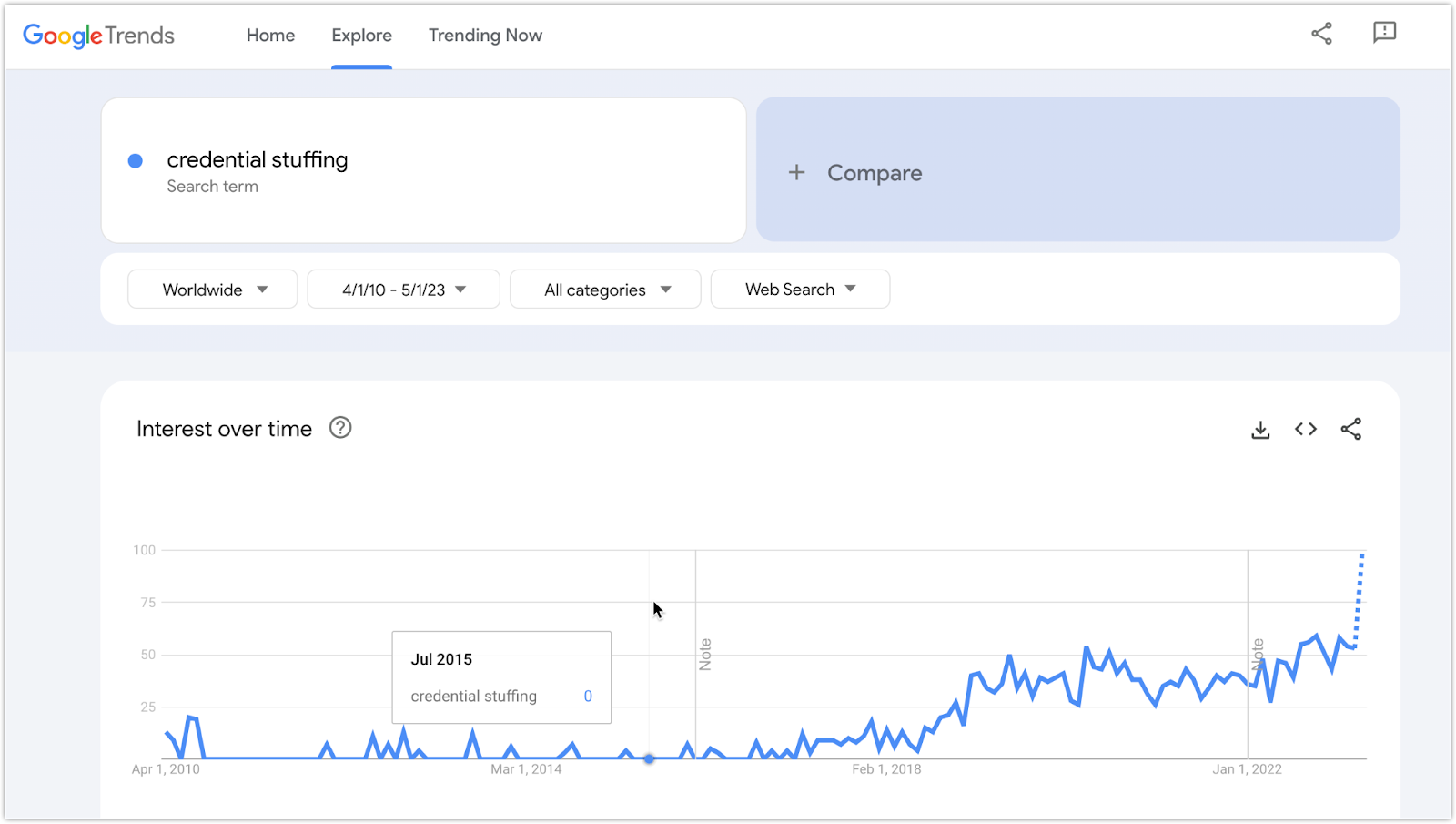
Alas, according to Google Trends, interest in the keyword “credential stuffing” and other related terms have been on an uptrend in the past few years (note: even starting pre-pandemic). With more employees now working remotely, logins to your public-facing sites/applications—as well as incidents of unauthorized access like credential stuffing attacks—are expected to increase.
3. VPN exploits
You typically use a virtual private network (VPN) to gain remote access to resources (files, applications, hosts, etc.) in your internal network. As the name suggests, a VPN gives you a semblance of being physically present in your internal network even if you’re actually connecting from, say, a hotel overseas.
While this unfettered access is certainly a major convenience for remote workers—and is the reason why VPN is the de-facto tool for remote access—it can also be a huge risk if the VPN is compromised. Threat actors may exploit vulnerabilities in your VPN to bypass authentication methods, execute arbitrary code, or perform other malicious acts that then enable those crooks to gain unauthorized and unmitigated access to your network.
4. Insecure applications
In many remote work set ups, remote workers are allowed to use personal mobile devices (i.e., personal laptops, phones, tablets) to accomplish work-related tasks. Because most of these devices aren’t managed by IT departments, users are free to install whatever software applications catch their fancy. Some of these applications can be either insecure or just downright malicious.
When used alongside legitimate programs used for work, these insecure/malicious applications pose a security threat to company data stored on those personal devices. Also, the moment those users walk back into your office, they’ll be bringing those insecure/malicious apps with them. That behavior will give threat actors a path into your internal network.
5. Ransomware attacks
Findings from the 2022 Verizon Data Breach Investigations Report showed an approximately 13% increase in ransomware-related breaches—equivalent to the yearly increases in the last 5 years combined. Since ransomware typically find their way to endpoint devices through poor end user security practices like clicking on unverified links in emails, disregarding patches, performing online transactions on public Wi-Fi, and so on, I expect remote workers to be more susceptible to ransomware attacks.
The reason is because, unlike in office environments, remote workers are—as I said earlier—no longer under the watchful eyes of your IT/security team and the protection of your firewall and other security solutions.
Protect your remote work environments with Intrusion
Keeping remote workers safe from cyber threats can be a tall order. It requires new security models like Zero Trust that take into account the perimeterless nature of today’s work environments. It also requires greater protection on mobile devices, which are increasingly being used by remote workers to access resources in your corporate network.
Here at Intrusion, we’ve developed a new paradigm for zero trust as well as a mobile security solution that can help you protect your remote work environments from cyber threats. Click the chat button at the lower-right corner of your screen to learn more.


