
Top 5 Endpoint Security Threats to Watch For in 2023
Increased adoption of remote/hybrid work and Bring Your Own Device (BYOD) practices is exposing users and endpoint devices to more cyber threats than ever before. These practices are widening your attack surface and making it substantially more difficult for your IT admins and cybersecurity staff to secure your organization.
Remote workers, for example, spend most if not all of their time outside your corporate firewall. In most cases, they use their own personal devices for work-related tasks. Many of these devices are outside the purview of your IT department. In other words, they’re likely unmanaged, unmonitored, and unsecured. As such, these devices are highly vulnerable to threat actors on the prowl for low-lying fruit.
That said, even endpoint devices inside your corporate firewall aren’t completely immune to cyber threats. In this post, we’ll take a look at what we believe are the top 5 threats to endpoint devices that you’re bound to encounter in the succeeding months.
1. Ransomware
Ransomware attacks continue to grow at an alarming pace, with the 2022 Cost of a Data Breach report showing a 41% growth rate for ransomware-related data breaches compared to the previous year. This development doesn’t bode well for organizations that rely heavily on IT systems to operate (who doesn’t these days?). Once a ransomware outbreak spreads through your network, practically your entire business can be held hostage.
Most ransomware are designed to encrypt data files and render those files inaccessible, so they usually infect servers, PCs, laptops, and mobile devices. The Rackspace ransomware attack in December last year, for instance, targeted Microsoft Exchange servers. On the other hand, the attack that disrupted several Sobeys outlets in November mainly affected in-store computers.
One of the reasons we’re seeing an upsurge in ransomware incidents is because ransomware-as-a-service (RaaS) has lowered the barrier to entry into the ransomware industry. In the past, only certain cybercrime gangs were capable of launching ransomware attacks. Today, anyone with enough financial resources can subscribe with a RaaS provider and carry out attacks through that service.
RaaS is just like any as-a-service offering. You can get 24/7 tech support, documentation, a knowledgebase, a command-and-control dashboard, subscription-based pricing, etc. Some RaaS providers even offer penetration testing, victim analysis, and negotiation services. All these features combined with the potential ROI of a ransomware operation will surely attract even non-tech-savvy criminals to do cybercrime.
2. Phishing
The number of detected phishing attacks hit a record high in the 3rd quarter of 2022. While the result for the 4th quarter hasn’t been released yet, we won’t be surprised if the number breaks the current record. For 5 consecutive quarters now, the Anti-Phishing Working Group (APWG) has been seeing not only record high phishing attacks, but also significant increases from previous records.
Below are the number of unique phishing web sites detected since Q1 2021 as per APWG. Each unique phishing site is considered one phishing attack.
| Quarter | Number of unique phishing web sites detected |
| Q1 2021 | 611,877 |
| Q2 2021 | 616,939 |
| Q3 2021 | 730,372 |
| Q4 2021 | 888,585 |
| Q1 2022 | 1,025,968 |
| Q2 2022 | 1,097,811 |
| Q3 2022 | 1,270,883 |
We’ve plotted those values to show the increasing trend.
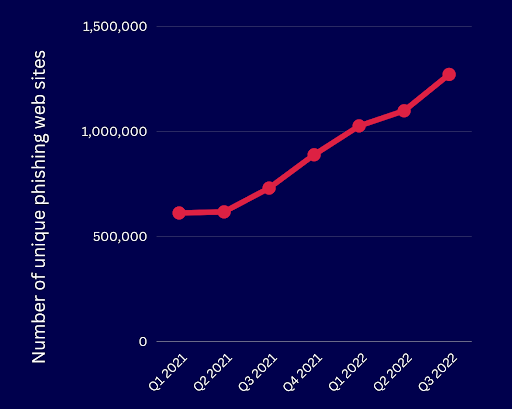
As the chart above illustrates, phishing attacks aren’t showing any signs of slowing down. In the 2022 Cost of a Data Breach report, phishing was found to be the second most common initial attack vector. Being an initial attack vector, phishing is employed by threat actors to gain an initial foothold into a target’s network.
This is done through either a malware infection when a user downloads an attachment accompanying the phishing email or through credential theft when a user unwittingly provides login credentials to a bogus webpage linked from the phishing email. Phishing attacks usually succeed because many users still find it hard to distinguish a phish from a legitimate email.
Indeed, even nation state threat actors (see discussion below) are known to use phishing as an initial attack vector in cyber warfare operations. Since these threat actors are also on the rise, we expect this trend to continue this year.
3. Insider Threats
Although less common than external threats, insider threats can cause greater harm to your organization. This is largely due to the fact that insiders already have access to your internal systems. Data from the 2022 Data Breach Investigations Report (DBIR) showed that the median number of compromised records in breaches involving insiders outnumbered those involving external threat actors more than 10 to one.
Insider threats typically come in one of three types:
- Malicious insiders – These are employees and contractors who have an axe to grind against your organization.
- Careless insiders – These are users who lack security awareness and hence either fall for a simple social engineering attack or accidentally expose company data through misconfiguration.
- Compromised insiders – Not necessarily careless, this insider is one whose account has been compromised by a sophisticated hack.
Last year’s Uber hack, one of the most high profile cyber attacks of 2022, happened due to a compromised contractor. The hacker, who already acquired the contractor’s username and password from a previous malware attack, managed to beat Uber’s multi-factor authentication (MFA) system by bombarding the contractor with sign-in requests.
As soon as the contractor approved the request (partly due to exhaustion from the barrage of requests and partly after being tricked that the request came from Uber’s IT team), the hacker took over the contractor’s account. The hacker then performed lateral movement to access other systems in Uber’s network.
With 74% of respondents in the 2023 Insider Threat Report indicating that insider-related attacks have become more frequent in the last 12 months, we expect this trend to continue well into 2023.
4. Zero-Day Exploits
Emerging secure development strategies like DevSecOps, which are designed to introduce security early in the software development lifecycle (SDLC), should dramatically reduce vulnerabilities in software. So far, however, DevSecOps adoption has been quite low. A report released last year showed that only 22% of respondent organizations had adopted a formal DevSecOps strategy.
That’s why, despite current best efforts in the industry, zero-day vulnerabilities continue to exist. That’s even an understatement. In VMware’s 2022 Global Incident Response Threat Report, 62% of respondents indicated having encountered zero-day exploits in the past 12 months. That amounted to an 11% increase from the previous year.
The risk introduced by zero-day vulnerabilities, i.e., vulnerabilities that are known to threat actors but have yet to be discovered by the security community, is further aggravated by poor patching practices. Many organizations take forever to implement patches. As such, even if a security update is already available, threat actors can continue to exploit the vulnerability that patch is supposed to fix.
If even IT staff are slow to apply patches, how much more regular end users? Many end users lack security awareness and, in turn, the sense of urgency to apply patches. This situation gets even worse in remote work scenarios where remote users largely operate with a high degree of autonomy.
5. Nation States
Ever since the start of the current Russia-Ukraine war, Russian state actors have been launching cyber attacks alongside military operations. A few hours before the initial offensive in February 2022, threat actors unleashed wiper malware on IT systems in Ukrainian government, communications, power, and financial institutions, causing major system failures and disruptions. Those distractions helped pave the way for the military invasion.
Nation state threats exist globally, with Microsoft also identifying threat groups from China, Iran, North Korea, and Lebanon in the 2022 Microsoft Digital Defense Report. The rise of nation state threats and the use of cyber warfare is taking cyber attacks to a whole new level. A state-backed threat group have substantially more resources at their disposal than other cybercrime organizations.
While the main targets of these cyber attacks are critical infrastructure as well as government and military systems, state actors often gain initial access by compromising users and endpoint devices through attack vectors like phishing and zero-day exploits. From there, they perform multiple lateral movement and privilege escalation maneuvers until they reach their ultimate objectives. State actors are willing to take these circuitous routes in order to avoid detection and attribution.
Similar doctrines have been the driving force behind many supply chain attacks like the SolarWinds hack and the FireEye hack. Nation state threats target suppliers in order to gain access to those suppliers’ downstream customers, which presumably include their main targets.
Geopolitical conflicts have always been happening since the dawn of human civilization. And now that cyber weapons are being added to every nation’s arsenal, state-sponsored cyber attacks will only get worse. As with all military wars, civilians and civilian property (in the case of cyberwarfare—users and endpoint devices) unavoidably become collateral damage.
Surely, the number of endpoint security threats far exceed the list we have here, and we’ll certainly cover them in later blog posts (if we haven’t yet). Nevertheless, adopting security measures against these top 5 threats can already significantly reduce your exposure to potential data breaches and cyber incidents.
Recommendations
Many threats to endpoint devices involve inbound/outbound connections from/to malicious sites. One way to counter these threats is by implementing Intrusion’s endpoint security solution, Shield Endpoint.
Shield Endpoint enables real-time inspection of inbound and outbound connections, leveraging Intrusion’s Global Threat Engine, which possesses historical knowledge of billions of domains and IPs. It uses this knowledge to instantly identify and block malicious or unknown connections from any device.
Designed to support remote/hybrid and BYOD environments, Shield Endpoint offers centralized security for your distributed workforce. You can use it to enhance your BYOD policies, and discover, monitor, and protect device connections wherever those devices are.
Not sure if Shield Endpoint is right for your organization? Let’s talk. Our security experts will be happy to help you determine that.


