On-premise network protection
Meet your always-on threat analyst.
In cybersecurity, speed is critical. Shield OnPremise helps you understand your environment’s biggest threats, fast.

There’s malware in your network.
We help expose it. Take a tour of Shield OnPremise below.
Shield OnPremise exposes threats you never knew existed.
Powered by our Global Threat Engine, Shield OnPremise sits behind your firewall. Trusted IP connections are permitted. Malicious connections are blocked. Security teams love it.
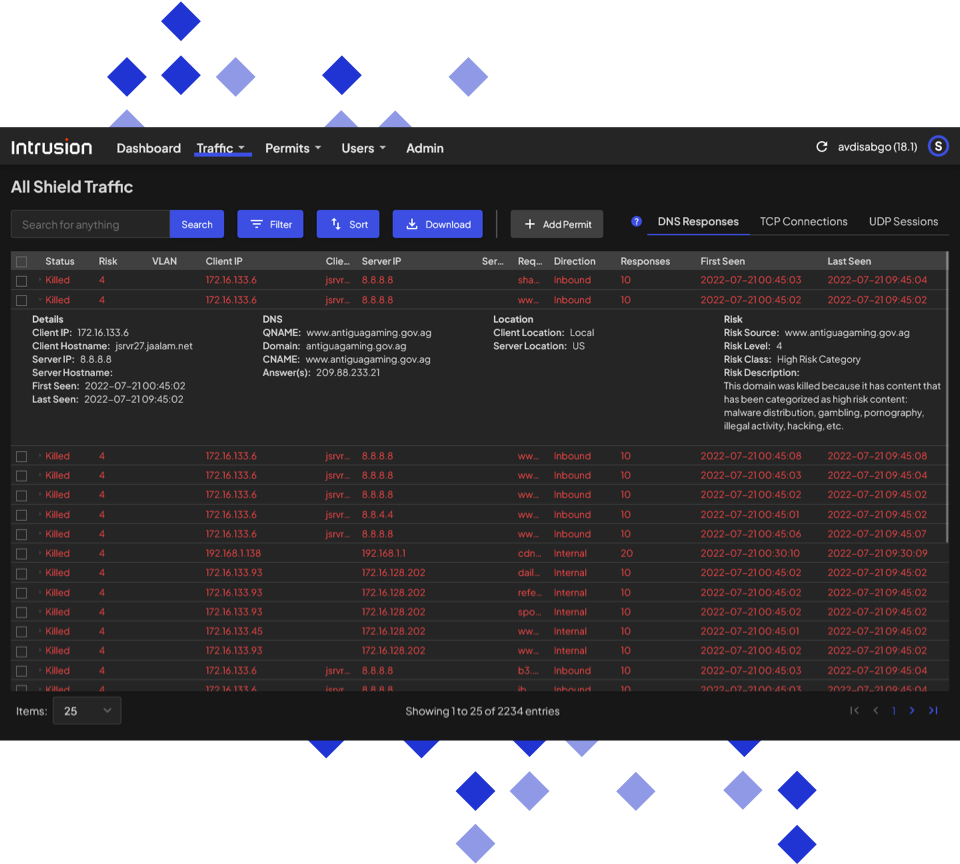
See all inbound and
outbound blocks.
See the real-time list of all blocked connections. Drill down on an individual connection to see more details like why it was blocked, risk level, etc.
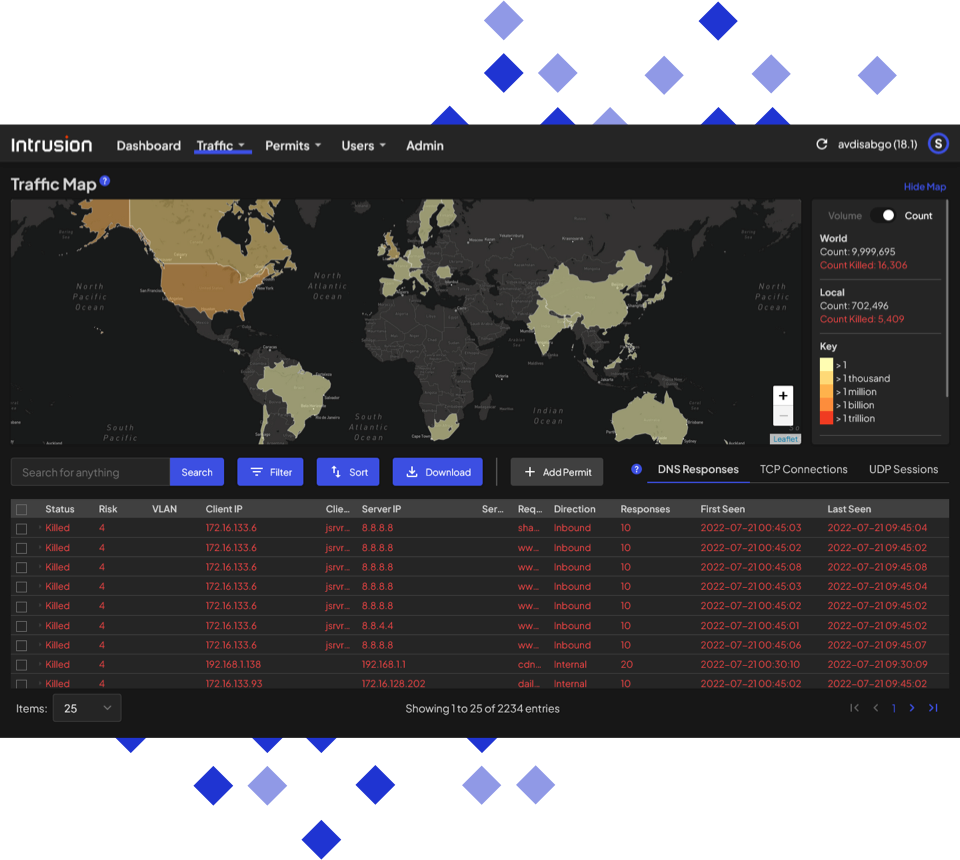
Find out where connections are coming from.
An interactive map shows you what countries your business is communicating with the most.
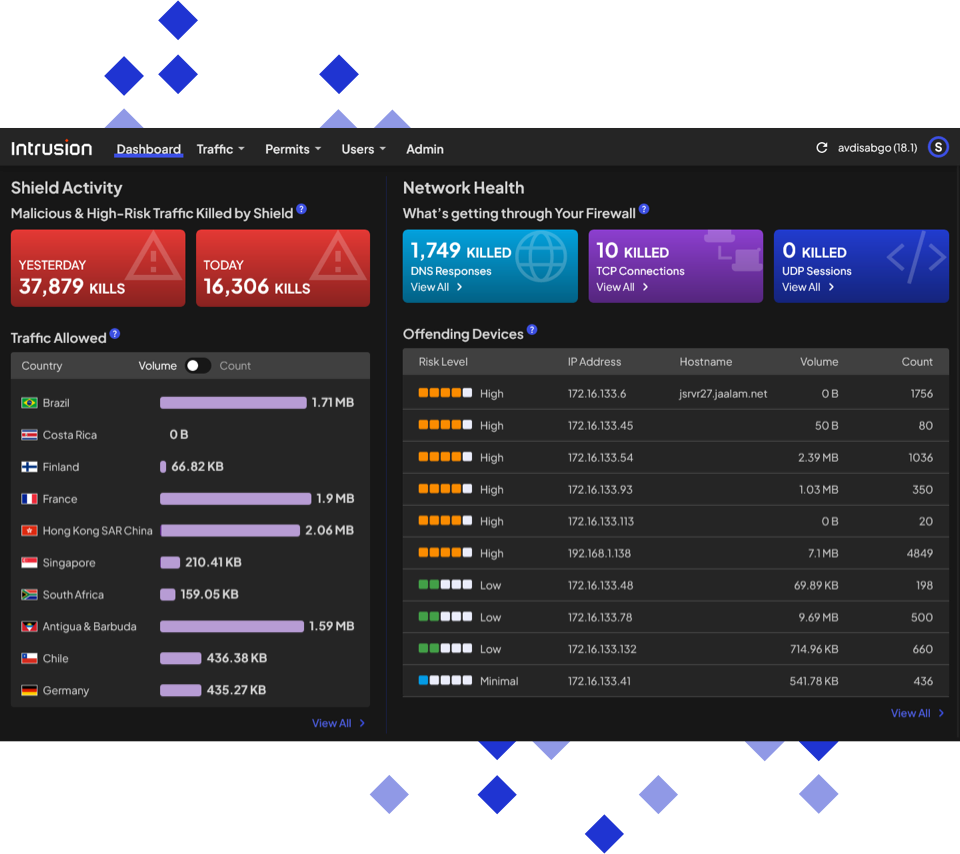
Identify the top offending devices.
Quickly see which devices have the most malicious connection attempts to prioritize remediation efforts.
We don’t fit in a box
Shield OnPremise sounds a lot like other types of solutions, but we don’t fit neatly in a box.
How Shield is different than a firewall
How Shield is different than a firewall
How Shield is different than an NDR
How Shield is different than an NDR
How Shield is different than an IDS/IPS
How Shield is different than an IDS/IPS
Less reacting. More protecting.

See every connection
If an IP is trying to connect, you’ll see it. Shield OnPremise monitors traffic bidirectionally in real-time, giving you full visibility of every connection being made on your network.
Know the good
from the bad
Stop guessing which connections are actual threats. Informed by decades of historical IP records and reputation in the Global Threat Engine, Shield OnPremise instantly identifies malicious or unknown connections in your network.

Protect your network and your team
Reduce cyber security team burnout and alert fatigue with autonomous real-time network monitoring and 24/7 protection. Shield OnPremise blocks malicious connections and enables your team to methodically prioritize threat resolution, without generating alerts.
Increase protection from Zero Days
Most companies simply don’t have enough historical data to classify connections as good or bad. Since blocking everything would bring your business to a standstill, Zero Day threats settle in undetected. Shield OnPremise gives you the historical data you need to identify and block potentially malicious connections without impeding the good ones.

Strengthen your existing security systems
Shield OnPremise seamlessly integrates into your existing environment and takes the burden off of your technology, SOC, and IT teams and other security products so they can perform better. Over time, Shield OnPremise can take the place of other products allowing you to consolidate your tech stack.
What customers are saying…

