To log into the Shield Dashboard, launch a web browser and enter: dashboard.intrusion.com.
If the page is unreachable, enter the IP address that was assigned to the Shield’s Management port instead.
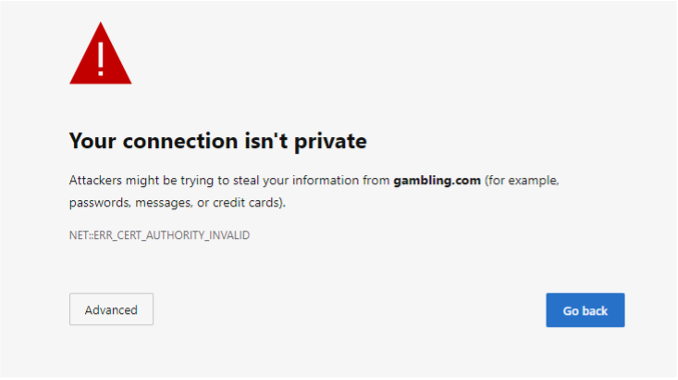
Upon successful connection to the Shield, a warning labeled “Your connection isn’t private” will be displayed.
This is because Shield uses a self-signed certificate.
Click Advanced to proceed.
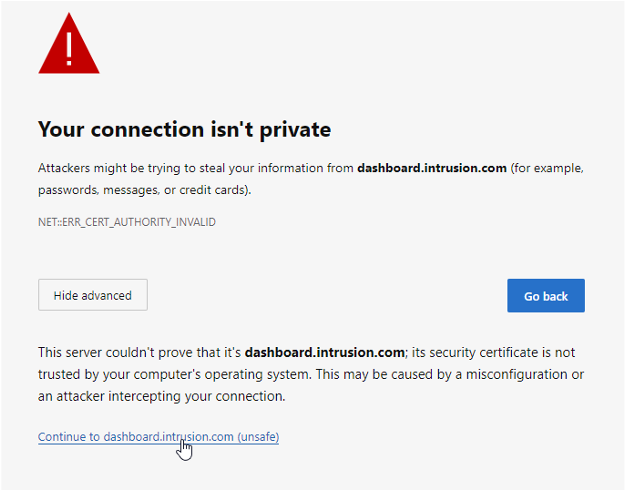
Next, click Continue to dashboard.intrusion.com (unsafe)
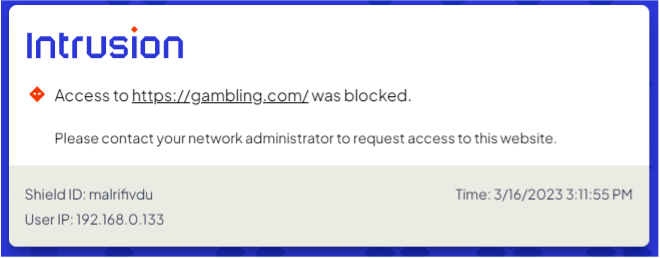
The dashboard login page should now accessible. Use the username and password that you received from Intrusion. If you don’t have this information, please contact customer support.
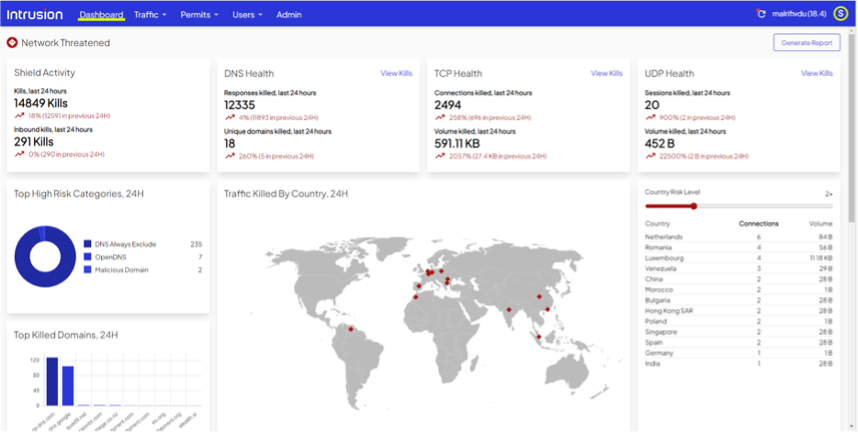
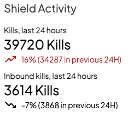
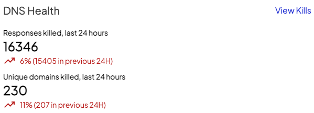
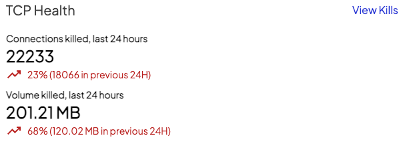
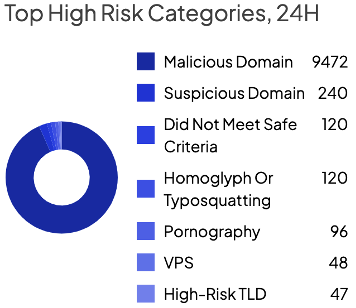
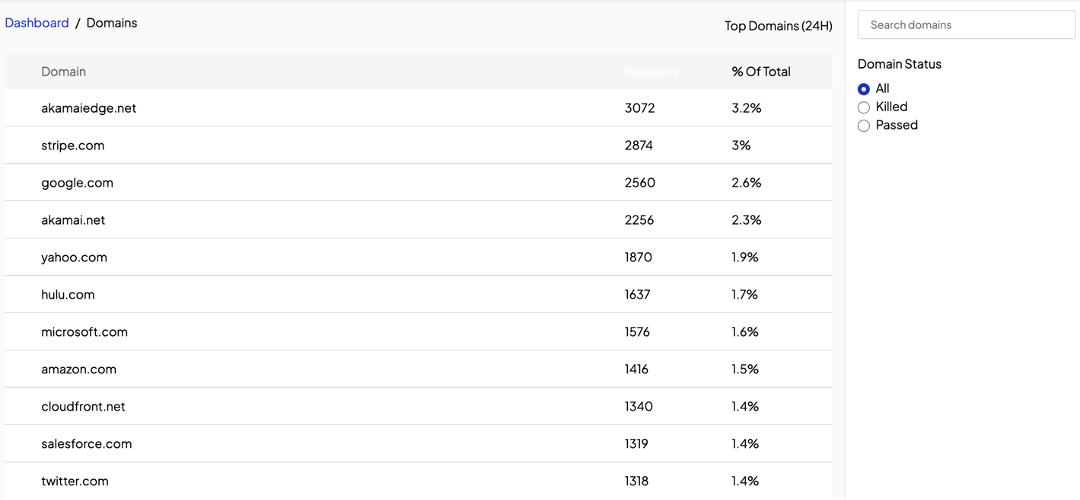
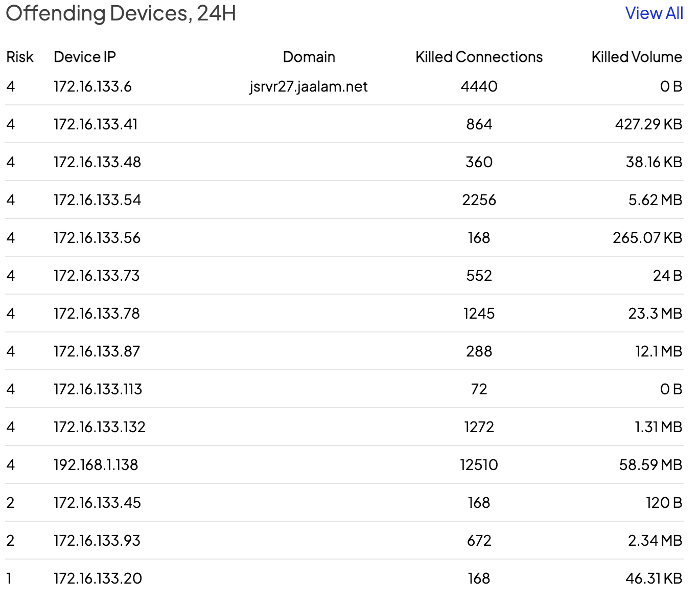
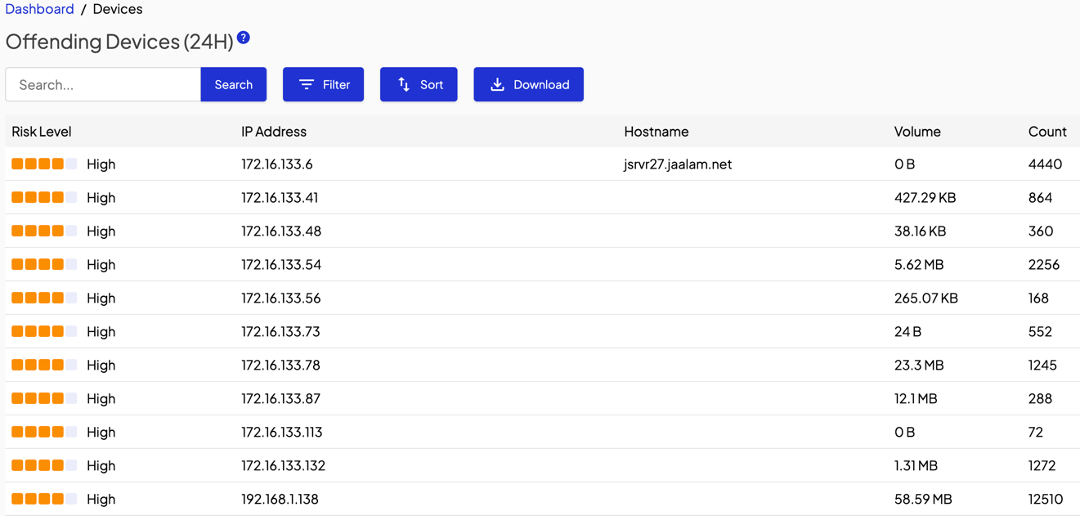
Once you’re logged in, the main dashboard should be visible. The dashboard will give you an overview of key security-related information generated by the Shield in the last 24 hours. This information should instantly refresh your situational awareness, enabling you to gauge your current security posture at a glance.
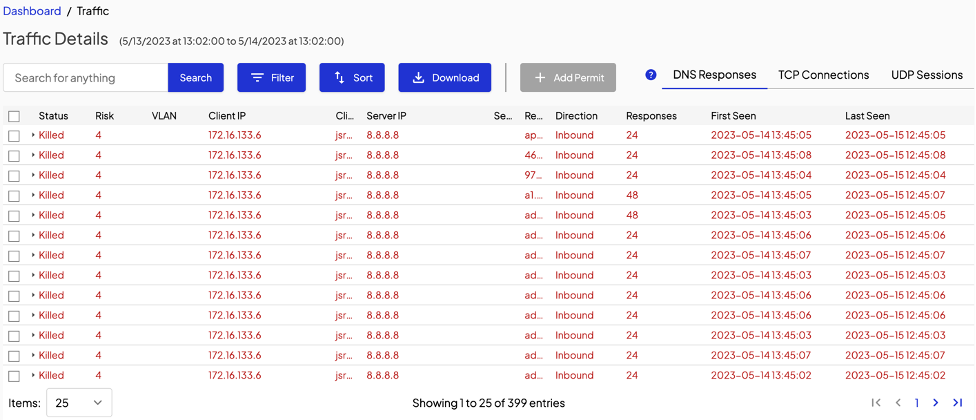
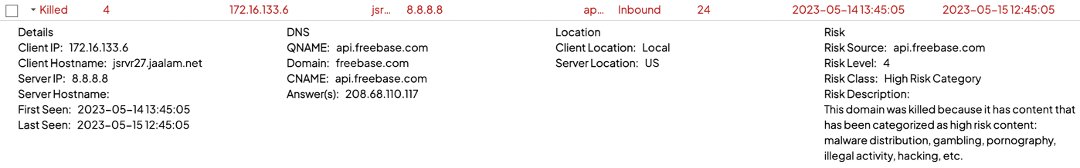
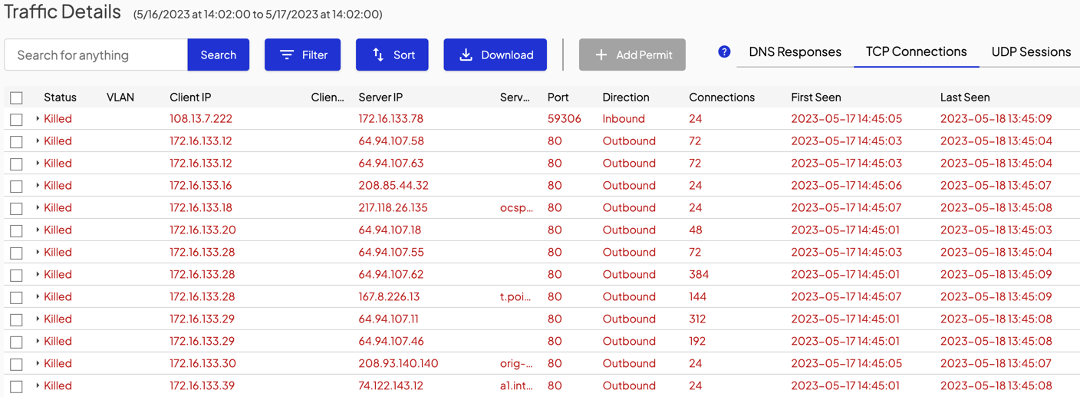
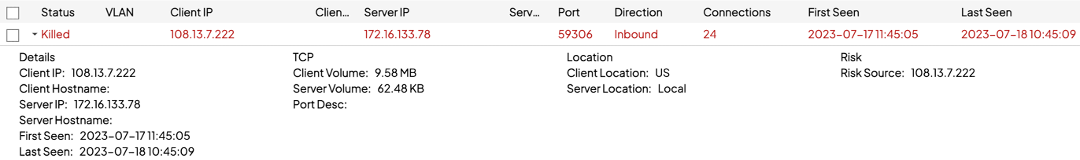

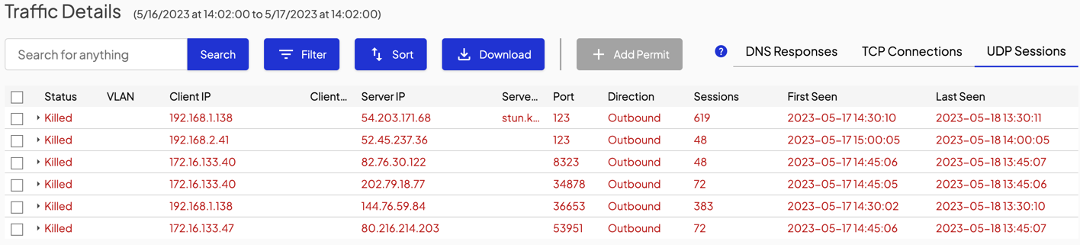
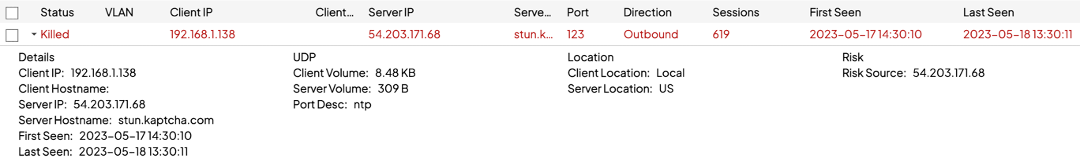
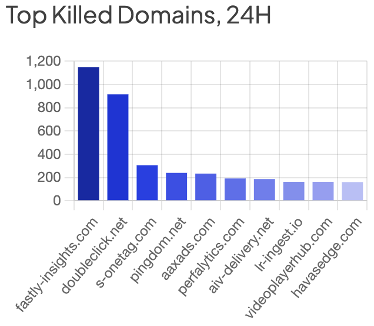
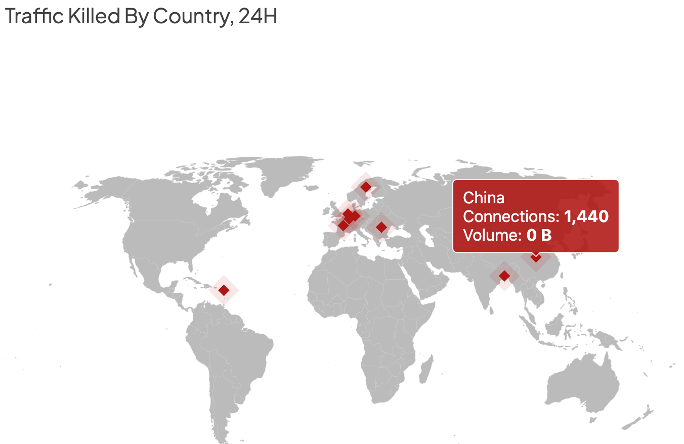
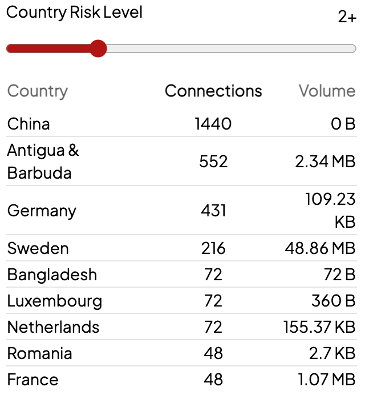
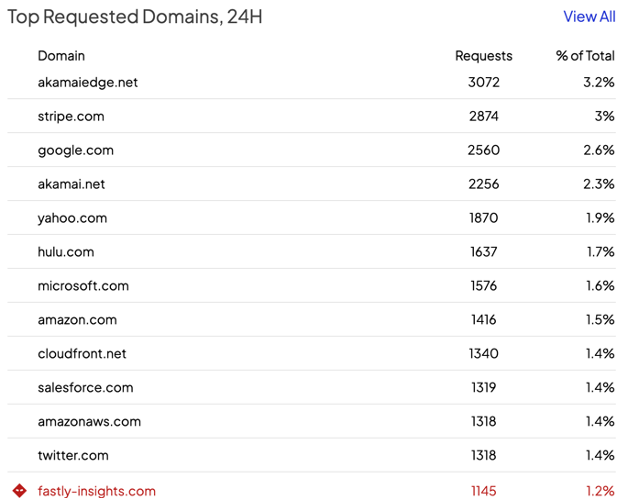
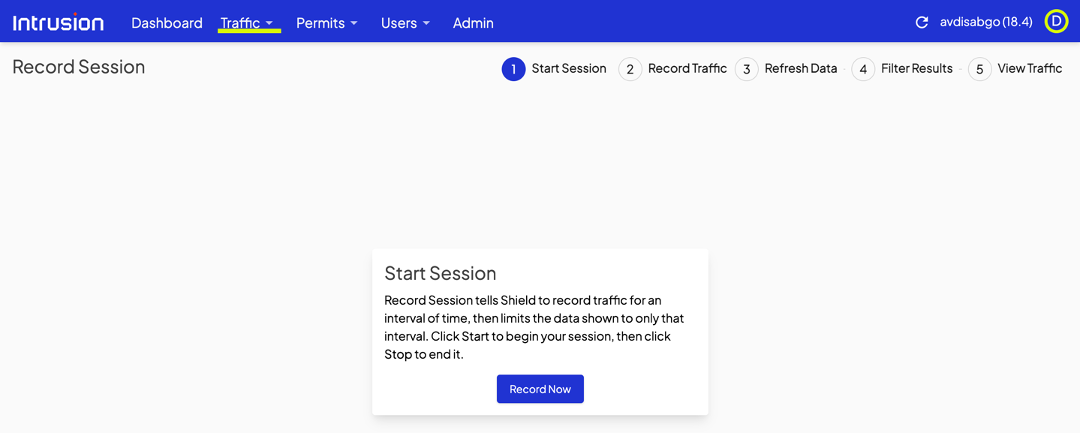
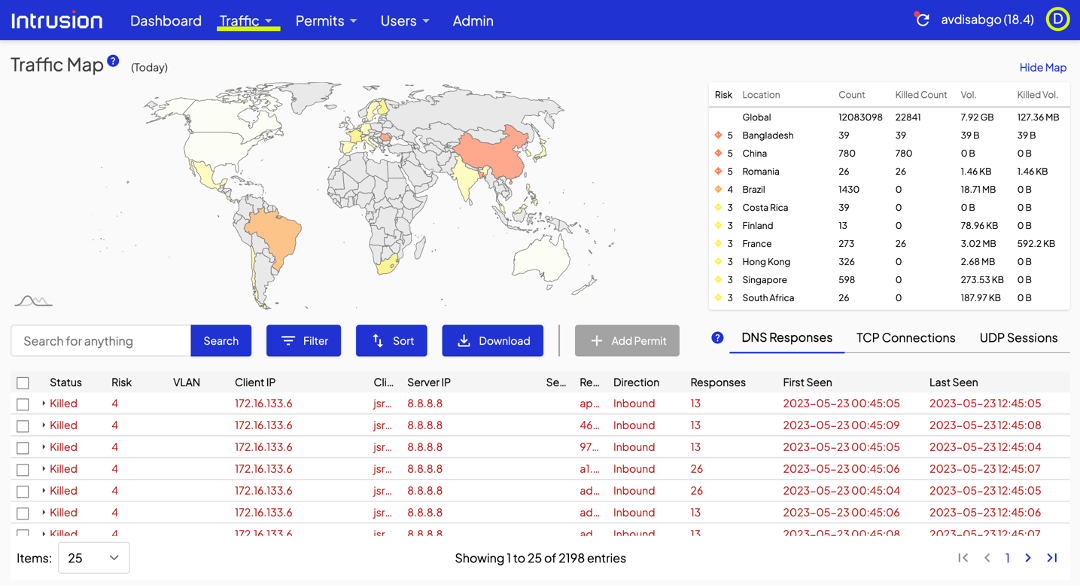
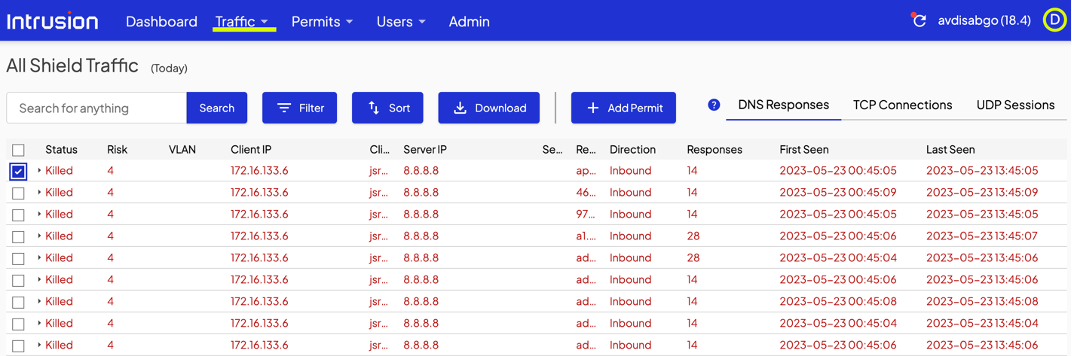
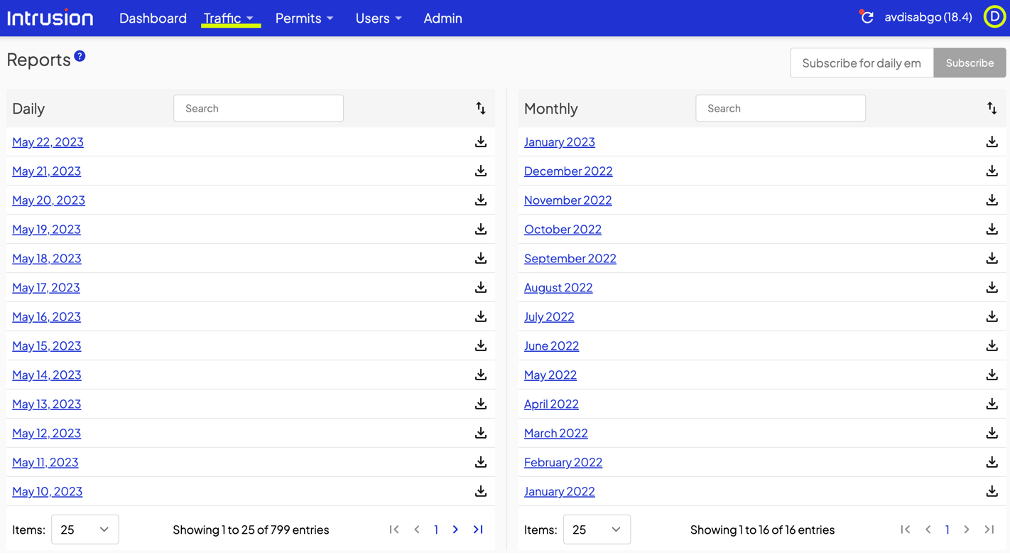
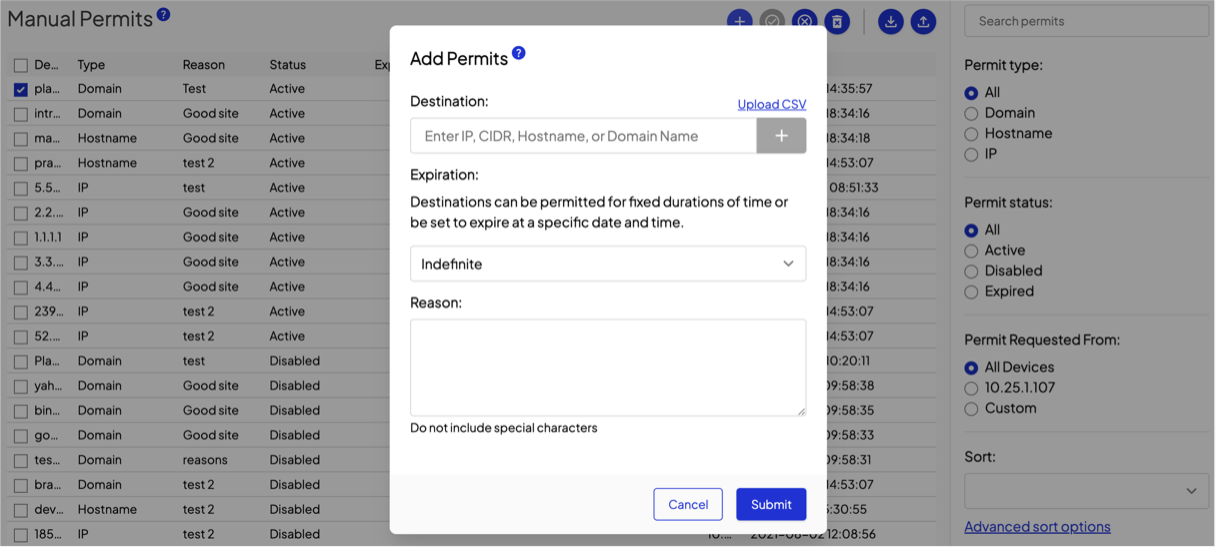
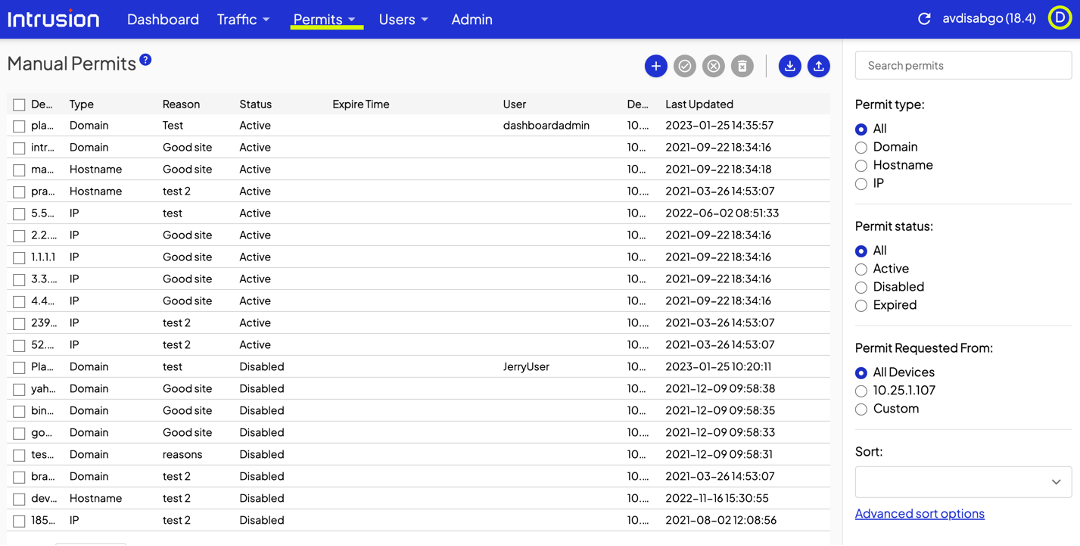
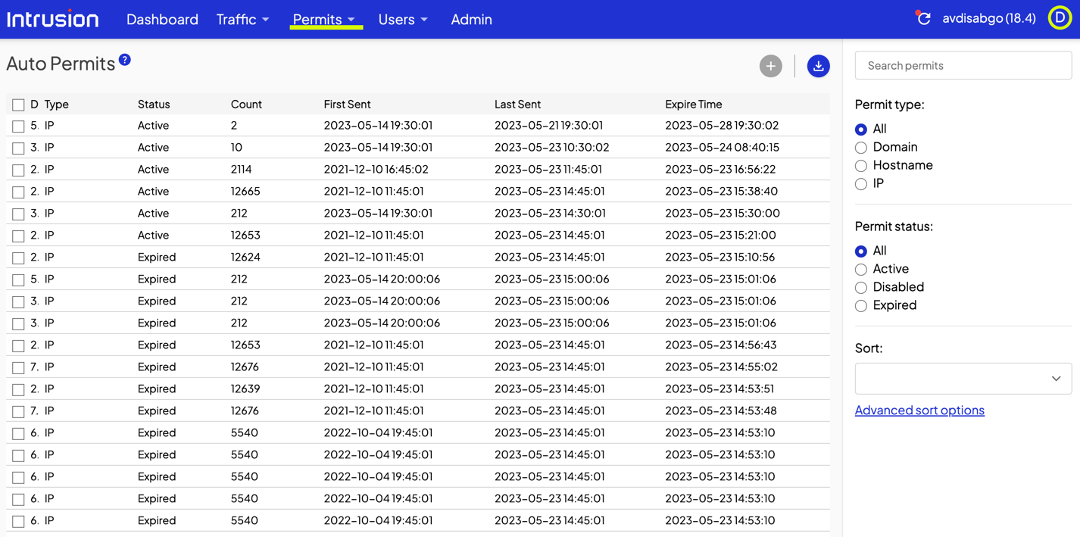
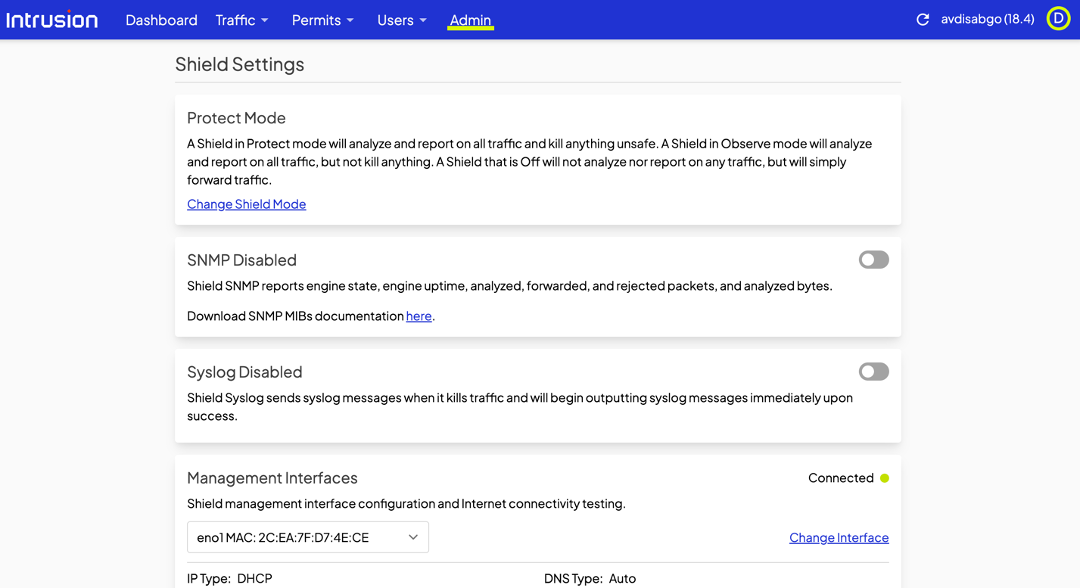


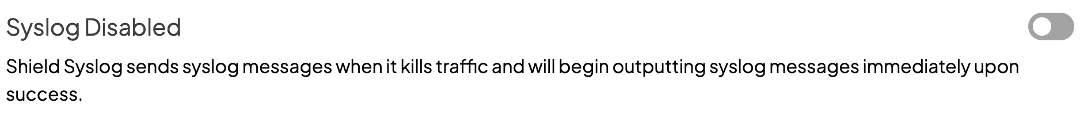
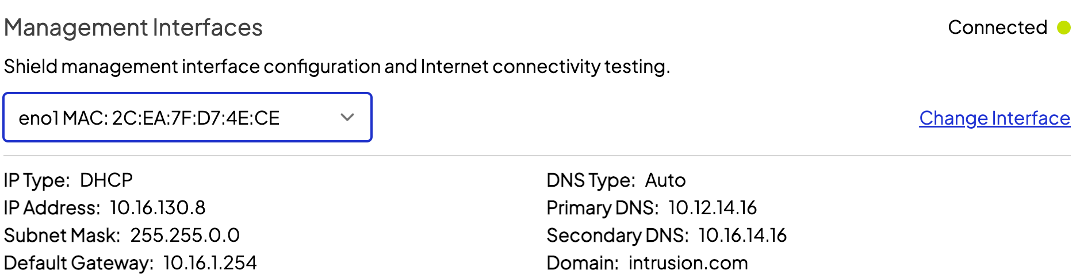


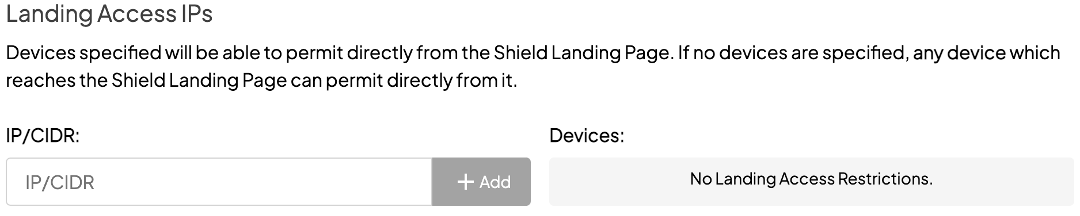

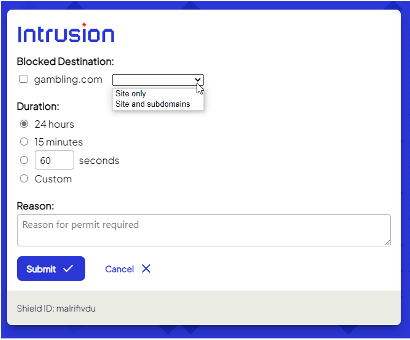
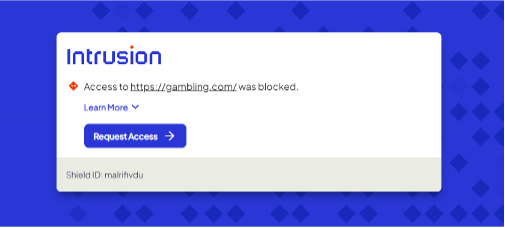 That user action will prompt the Shield to present you, the admin, a dialogue that looks very similar to the manual permit page in the dashboard. Check the connections to permit a specific site only or the site and all its subdomains.
That user action will prompt the Shield to present you, the admin, a dialogue that looks very similar to the manual permit page in the dashboard. Check the connections to permit a specific site only or the site and all its subdomains.