
There’s malware in your network
For a short period during the last half of 2021, it seemed like the world was getting ahead on cybercrime attacks like ransomware, data breaches, and malware. Several ransomware groups closed down operations because their members were arrested by Interpol, or the members turned on the group itself. However, this reduction in cybercrime criminal activity was short-lived and the groups were all back to regular operations within a few months. By June 2022 there were already 2800 victims of extortion sites run by 12 ransomware groups.
If you don’t believe malware is residing dormant inside your network just waiting, you’re not taking your cybersecurity seriously. Many people are surprised to find out that not only is malware in their system already, but it’s communicating with its command and control (C2) master slowly and quietly just waiting for attack instructions. It gets missed often because of over-reliance on detection and reporting solutions that don’t look in the right places to find them.
How do you get malware?
In 2017, DarkReading published a pair of articles detailing four standard malware practices used by hackers and advanced ways that they hide malware on unsuspecting systems. Despite being published 5 years ago, the tactics detailed by DarkReading are still prevalent today and still very successful with getting past all the latest cyber security solutions.
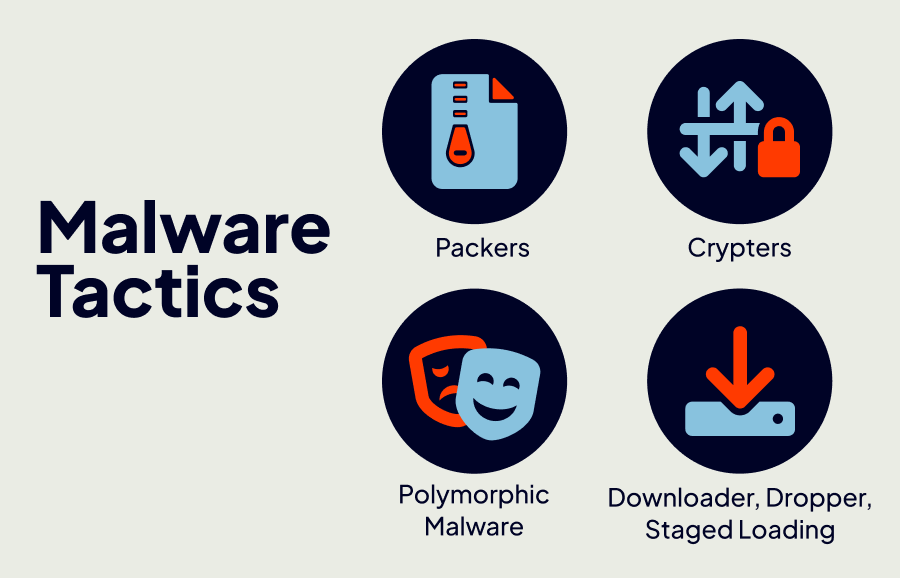
These methods are:
Packers – A program that makes an executable file smaller by compressing it allowing it to hide from detection.
Crypters – Similar to a packer, but includes an additional level of encryption on files to make detection even more difficult.
Polymorphic Malware – Program that utilizes both packing and crypting to continuously change its appearance and mutate itself when copied.
Downloaders, Droppers, and Staged Loading – Programs that do reconnaissance on a machine to collect information before malware is actually installed.
When malware is installed on your system it often doesn’t activate and attack your data on day one. It waits until it is activated by a trigger that is pre-programmed. This can be a countdown in the file set to run after a certain amount of time, a combination of certain actions completed by the user, or a call to its C2 server to get further instructions. Until it is activated it can lie quietly and undetected in your network indefinitely.
Where does it usually hide?
There are many places malware can hide in your network. Common hiding spots include Critical System Files, Windows Registry, Temporary Folders, shortcuts (.ink files), and common user files. Even programs that seem harmless can allow an easy opening for hackers and malware. For example, a recently discovered flaw in Microsoft Word uncovered a Zero-Day exploitation issue that could be used to gain access to a network. Not long after its discovery, researchers began seeing a growing list of IPs being used to search for these files across internet networks in hopes of exploiting them before a patch is released.
It is common for threat actors to obfuscate, encrypt, and embed malware files that appear to be legitimate.
This makes malware harder to locate because it is time-consuming for machines to compare files and determine if the original file has been tampered with due to the high volume of files that continuously move throughout a network.
How long does it sit in your network dormant?
There is no standard time frame for malware to lie dormant before being activated. It could be just a matter of a few days or even years. There has even been malware discovered after 6 years of lying dormant.
Malware will stay in your network until it is discovered or gets activated. Often it is detected too late or after some damage has occurred.
How can you detect it?
Knowing how threat actors can hide malware in your system and where to look for it helps create a solid foundation for detecting threats on your network. This information is what vendors when designing malware detection technology for networks. However, even the best of these solutions can’t stop every threat.
While most cybersecurity solutions protect by watching what comes into a network, we believe it is watching what goes out of a network that leads to the most successful outcomes.
This approach that assumes you already have malware inside your network. Inspecting every packet that exits your network allows you to quickly see what packets are being sent to high-risk IP addresses with low-reputation scores. This data can then be analyzed allowing you to trace the communication path back to its origin. Once you find the hiding spot of the hidden malware you can determine its purpose and locate any other instances on your network for your damage assessment and recovery operations.
The Intrusion Threat Engine contains historical data on over 3 trillion IPs, hostnames, and domains and evaluates the risk level. In almost every case to date, Intrusion Shield discovered malware that had slipped past network security and communicating to an external C2 server.
Please contact us if you’d like to learn more about how Intrusion’s expertise in applied IP reputation-based threat intelligence can help protect your business and reveal malware hiding in plain sight.


