
The Biggest Challenges for SOCs
In our State of Threat Hunting report, we identified the 5 top challenges facing Security Operations Centers (SOCs). According to the survey respondents, the biggest challenges are the following:
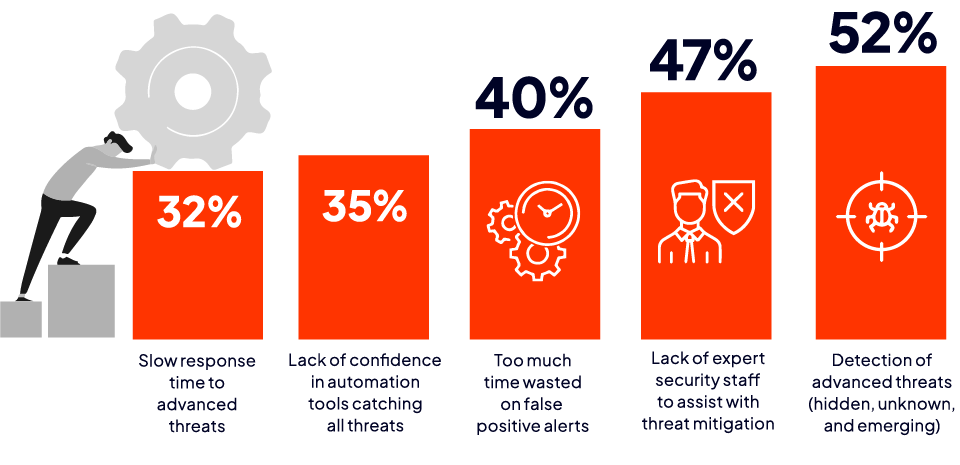
- Detection of advanced threats
- Lack of expert security staff to assist with threat mitigation
- Too much time wasted on false positive alerts
- Lack of confidence in automation tools catching all threats
- Slow response time to advanced threats
Let’s discuss these 5 challenges in more detail and explain why you need to address them.
1) Insufficient Ability to Detect Advanced Threats
Advanced threats that employ evasive techniques can defeat many threat detection tools in your SOC’s arsenal. In the past, highly sophisticated cyber attacks were exclusively the handiwork of organized cybercrime groups. Today, however, advanced cyber attacks can also come from a more sinister adversary. The arrival of nation state threat actors has radically changed the cyber threat landscape for the worse.
Equipped with immense human, technological, and financial capital, these actors are capable of deploying advanced persistent threats (APTs), mostly for espionage and sabotage campaigns. APTs are deeply-covert threat groups that can infiltrate heavily defended infrastructures and persist in those environments for as long as they need to. With the 2022 Microsoft Digital Defense Report declaring that cyber attacks from nation state threat groups have grown more sophisticated, the need to detect advanced threats has become even more critical.
For your SOC to detect these highly sophisticated threats, you need capable but usually cost-prohibitive threat detection tools. You also need the expertise to use them. Without the required expertise, your security tools can’t be optimized to detect APTs and other advanced threats. Alas, that’s a serious problem by itself. Let’s talk about that challenge next.
2) Lack of Expert Security Staff for Threat Mitigation
Organizations are currently grappling with a cybersecurity skills gap that left 3.5 million cybersecurity positions unfilled last year. Even if you wanted to hire cybersecurity staff for your SOC and could afford it, no one is available.
This deficiency is further aggravated by increased adoption of work practices like remote work and bring your own device (BYOD) as well as technologies like cloud computing and mobile, which not only widen your attack surface but also increase complexity in your overall IT environment.
Factoring in these new practices and technological advancements into your threat mitigation initiatives naturally require additional expertise and head count. If you’re already suffering from inadequate cybersecurity staffing, you’ll leave a lot of vulnerabilities open to exploits, security issues unattended, and security tools grossly underutilized.
3) Too Much Time Wasted On False Positive Alerts
The growing sophistication and variety of threats coupled with the steady barrage of marketing campaigns from security vendors has pushed organizations to accumulate an arsenal of security tools. Organizations now have an average of 76 tools, many of which generate a ton of alerts—and a substantial portion are just false positives.
Having to triage, enrich, process and analyze legitimate alerts alone can already be overwhelming. How much more if you also have to deal with false positives? False positive alerts can prevent you from analyzing and identifying an ongoing cyber attack. It can mislead analysts into embarking on a useless, resource-draining wild good chase.
Not only that, too many false positives can also make your SOC analysts more susceptible to alert fatigue. Once alert fatigue sets in, security staff become frustrated, stressed, and susceptible to burnout. This can in turn force staff to switch off alerts (which then enables more threats to avoid detection) or worse, leave your organization for more favorable working conditions.
4) Lack of Confidence in Automation Tools Catching All Threats
Automation is critical to security operations. By automating workflows and playbooks, SOC analysts can reduce time spent on certain functions like threat intelligence, threat monitoring, threat detection, threat analysis, incident response, and so on. It helps improve speed and efficiency in performing tasks. So, in a way, automation helps address the cybersecurity talent shortage problem.
But there’s a hitch. Automation is highly dependent on the reliability of its individual components. For example, if the alert data used in detecting a threat mostly consist of false positives, it will only mislead and confuse threat analysts. Similarly, if you’re overly reliant on the automated process and it’s actually generating a ton of false negatives, you’ll just acquire a false sense of security.
That said, you shouldn’t disregard automation altogether. You need it to counter advanced threats, which themselves employ automation and even artificial intelligence (AI) and machine learning (ML). Some threat actors may even use readily available AI tools like ChatGPT to synthesize malware. Indeed, automation is critical to SecOps. Just be sure you verify the reliability of the automation tools you use.
5) Slow Response Time to Advanced Threats
False positives and the lack of reliable automated threat detection tools prevent security staff from responding promptly to advanced threats. But the longer a cyber threat remains undetected, the greater its window of opportunity to inflict significant damage to your organization.
Sadly, in last year’s Cost of a Data Breach report, the average time to identify and contain a data breach was said to be 277 days. That’s just too long. The same report said that the average savings you gain from containing a breach in 200 days or less is $1.12M. Clearly, if you can reduce the time to detect and respond to a threat, you can enjoy substantial cost savings. Conversely, longer detection and response times equate to higher costs.
How Intrusion Helps You Address These Challenges
Security Operations Centers that face any or all of these challenges can benefit immensely from Intrusion. Intrusion solutions like Shield OnPremise employ applied threat intelligence (ATI) to inform their automated detection and response features.
ATI is an emerging class of security solutions that leverages threat intelligence (TI) but does away with a lot of the manual tasks associated with collecting, aggregating, enriching, and analyzing TI data. Moreover, ATI automatically utilizes threat intelligence data in detection and response. This essentially speeds up your SOC’s response time to advanced threats while eliminating unnecessary alerts. At the same time, ATI allows you to reduce and simplify your security team’s workload, and avoid having to hire new staff.
Would you like to know more about Intrusion and ATI? Click the blue icon on the lower-right corner of this page and chat with us now.


