
Morse code is now a trending encoding technique for hackers
Remember the History classes in high school where we learned that World War II warships used Morse code to communicate with each other? Morse code was a critical medium to send messages without using alphabets or numbers to hide them from third parties. Textually it can be defined as an encoding technique that only uses dots and dashes to transmit messages using sound waves, electric current, radio waves, or visible light.Cybersecurity technology is advancing daily, and so are the hackers upgrading their attacking tactics.
Using morse code in modern attack campaigns
If you were to ask if Morse code would be a trending topic today, I would have said absolutely not. However, hackers are using it in their new phishing campaigns. Recently, Microsoft confirmed that attackers are supplementing phishing attacks by sending detection evading and sophisticated emails to victims encoded in Morse code. Through these campaigns, the attackers’ goal is to acquire sensitive information like usernames, passwords, payment details, etc. Other data like location details and IP addresses facilitate the hackers for entering and exfiltrating the critical data.This attack pattern is unique and is considered equivalent to a jigsaw puzzle.
Decoding the attack
The hackers change their encryption and obfuscation every 37 days. The attacker’s motive is to lure the victim into falling for a financial-related email with an invoice theme. Finance emails are generally the best bait for phishing attempts. The attackers are using social-engineering techniques in an email comprised of an XLS.HTML file. The HTML file is further divided into various fragments that seem harmless but also contain embedded JavaScript files that run password crackers. When a victim opens this malicious attachment, a dummy Microsoft window pops up requesting to enter login credentials. If the victim is unlucky and falls for the gimmick, the pop-up displays that the login was timed out and asks to re-enter the credentials.
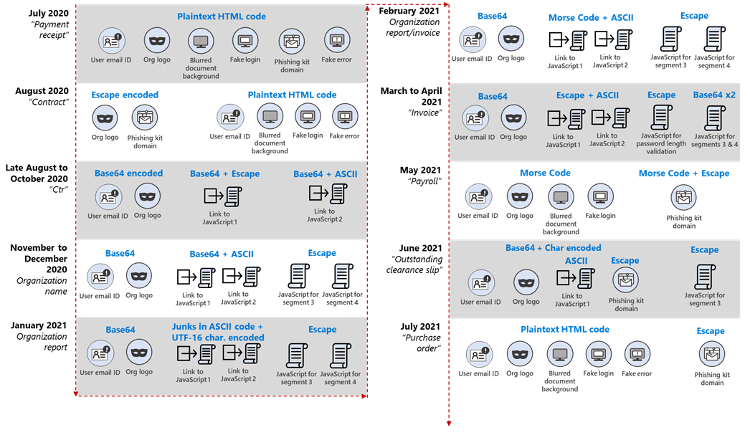
At the beginning of August 2020, the fake excel login page was removed from the email attachment and replaced with links to a website hosting the JavaScript. The robust encoding of these JavaScript files assists in evading security as they have a minimum of two layers of encoding. In November 2020, Microsoft’s Threat Team observed encoding of JavaScript files using Base64 and ASCII. In the samples observed in February 2021, the JavaScript file was first encoded using ASCII and again encoded using Morse code. In May, the HTML code was observed to be encoded using Morse code, and the domain name was encoded using Escape. Other researchers noticed that attackers used Morse code to hide malicious URLs in the form of dots and dashes. Soon after, a new information-stealing module was introduced that used the link “hxxps://showips[.]com/api/geoip/” to capture users’ IP address and Geo-location, which is sent and saved in the attacker’s C2 servers.
We have all encountered our share of phishing emails in our internet lives. Email security companies have been doing their best to prevent such mail from entering our inboxes. But no one could ever imagine or be prepared for all the varying, creative methods threat actors create to bypass the email filters. As long as there is email, they’ll keep at it. It’s easy to avoid phishing emails with the proper awareness, but the worrying thing is that highly equipped email security couldn’t readily recognize the threat in this case.
The good news
No matter how a phishing email evades security and lands in your inbox, and regardless of how many droppers and actions the embedded scripts can execute in memory while the user is logged on, eventually, the attack must call home to a C2 server.At the outermost layer of your enterprise or corporate network, packets with origination and destination information are transiting this layer as the attacker’s scripts or malware attempt to build that communications path. Interested in learning more about this path? Talk to one of our experts.

