
Here’s everything we know about BlackMatter
Didn’t we all hear that RaaS (Ransomware-as-a-Service) affiliates Darkside and REvil had recently ceased their activities? While threat researchers presumed those threat actors took an extended vacation from their activities, the chatter is that BlackMatter, a new ransomware organization, claims to be the descendant of DarkSide and REvil. These two notorious ransomware syndicates went dark after recent, massive attacks on Colonial Pipeline, JBS, and Kaseya.
Since the end of July, the group has posted advertisements on the dark web in the elite cybercrime forums: XSS and Exploit. Their ad said they were looking to hire affiliates with access to corporate networks in the United States, United Kingdom, Canada, and Australia with a minimum of $100 million in revenue. BlackMatter has not entirely revealed their intentions on the forum as they must abide by the forum’s rules. Still, the language in the ad indicates they are still Ransomware operators.
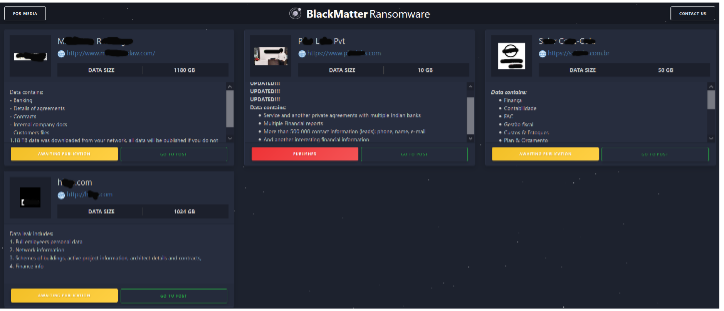
An interview with BlackMatter
Experts took note of BlackMatter and were able to interview a representative of the group. In it, they said they had combined features of Lockbit 2.0, REvil, and Darkside. Additionally, they have learned from the mistakes of these groups and won’t repeat them in their operations. It took them six months to develop BlackMatter, and they have already attacked various organizations. Most of the attack victims made their ransomware payments. According to BlackMatter’s terms of functioning, they post a blog only when an organization refuses to pay the ransom in the given time frame. Researchers at Intrusion found that BlackMatter’s website had a published blog just a few weeks after their interview.The published blog is of an Indian financial company whose data is now available to download.
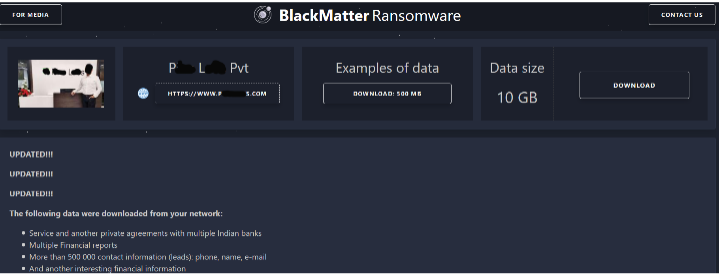
BlackMatter claims their targets differ from Darkside and REvil, and indicate they will not target the healthcare industry, government, critical infrastructure, defense, oil, and gas industry. We suspect other organizations like a Brazilian solar company, a mid-size law firm, and an architectural firm in Florida have their clocks ticking to pay a ransom, or their data will also be publicly available. Although we cannot validate any of these attacks, DarkMatter has released specific sample images from seized data as proof that their data was withheld information like financial reports, bank details, agreements, confidential contracts, employee details, etc., are released.
The makings of their ransomware
On further research, experts found that this Ransomware extracts information from the victim’s machine such as the hostname, user logged-in, the operating system used, domain name, system architecture, language used by the system, size of the disc, and freely available space. It sends this information to a C2 server, which is hosted on paymenthacks.com. It uses the same privilege escalation method used by Lockbit 2.0 and Darkside. BlackMatter uses old conceptual methods to obscure encrypted configuration information stored in a specific area, plus string encryption, and they obfuscate API calls, resembling old ransomware gangs.
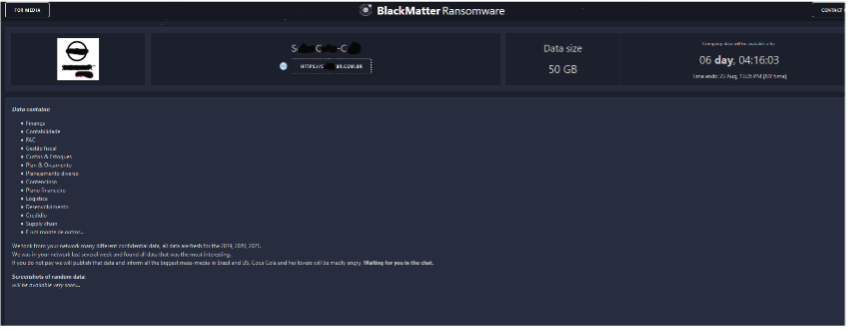
BlackMatter claimed to encrypt Operating systems and architecture of diverse types like Windows systems using SafeMode, Linux OS’s like Ubuntu, Debian, CentOS, VMWare ESXi 5+ virtual endpoints, and NAS devices like FreeNAS and TrueNAS. Recently, it had started operations to build a Linux encryptor for VMware’s ESXi platform. Many organizations are progressing towards virtual machines on company servers for improving the management of resources and easy recovery in case of disasters.
With the frequent ransomware attacks on major US organizations, President Biden had asked Russian President Putin to investigate the suspected RaaS operators Darkside and REvil operating within Russia’s border. Soon after this, we all heard about the disappearance of these groups. Darkside ended its operations after it lost access to its payment server, blog, and funds. A REvil representative named “Unknown” was the first to report it on a hacker forum. Two months after this, REvil had shut down its operation after the Kaseya attack. From the information found by security researchers, similarities in the activity found on websites indicate that the creator of BlackMatter was previously involved in the ransomware activities of DarkSide and REvil.
This Ransomware may do significant damage without triggering any warnings if an expert attacker uses it. The organizations defending their infrastructure need to evaluate protection devices immediately because they might have to bear the devastating effects. However, as with all ransomware criminal operations, the attack has to originate and come from somewhere, establishing a communications path between the attacker and victim. AI-leveraged security focused on these connections at the network layer can help.

