
Are your IoT devices leaving you vulnerable to cyberattacks?
Can you imagine saying “Okay Google, minimize global cyberattacks.” Or “Hey Siri, block all dangerous DNS requests.” Or “Alexa, can you reset my firewall to maximum security?” We all wish it were that easy to control our security posture – especially corporate SOC operators, who already have enough on their plate, that now have to worry about IoT devices permeating the companies network.
Nowadays, Internet-of-Things (IoT) devices are increasing in industries, manufacturing, home entertainment, hospitals, etc. Hot gadgets are making their way into the modern lifestyle; devices from voice assistants to smart-watches have made everyone dependent on internet-run technology. With the global number of installed IoT devices reaching 27.5 billion at the end of 2020 and doubling to 45.9 billion by 2025, this is indeed a big problem. People are in love with “smart homes,” laden with security cameras, refrigerators, other appliances, smart cars, etc. But they aren’t concerned about their privacy and security.
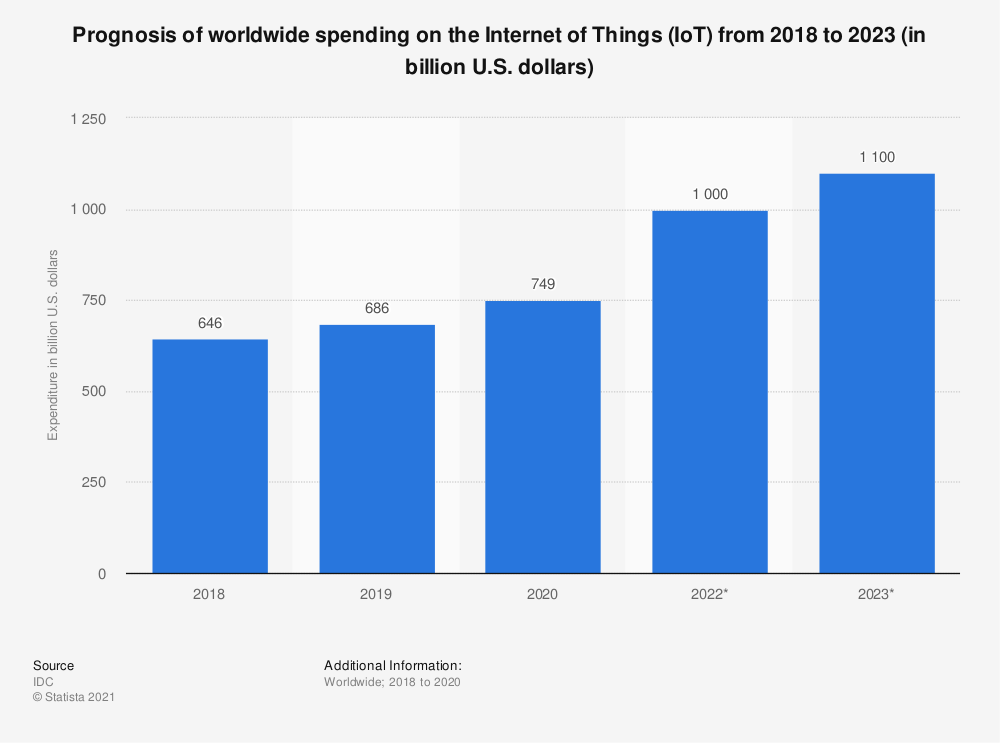
IoT devices are mass-produced, which means that attackers can exploit the same vulnerabilities in multiple devices due to supply chain attacks that embed code in the chips during the manufacturing and assembly process. Statista predicts that worldwide technological spending on IoT will reach nearly 1.1 trillion U.S dollars by 2023. Despite a dip in 2019 and 2020 (primarily due to Covid-19), an Industry Week report based on a survey of 442 manufacturing industry respondents indicates 31% say an impediment to growth is lack of technology, including automation and Internet of Things (IoT).
Organizations are developing newer IoT devices but are lagging in keeping up with their security updates. Running behind on releasing timely security patches can leave the device’s firmware vulnerable. This in turn can make the device the primary point of attack. Many corporate organizations have hugely benefited after the implementation of IoT for connecting remotely working employees. But the trade-off here is that these organizations already have their hands so full securing traditional technology that IoT security has been the least of their concerns.
With the proliferating IoT market, security incidents have drastically increased. Threats to IoT devices have escalated by 400% due to the availability of devices and lack of security. The threat actors have upped their game by attacking IoT devices with botnets like Mirai and Mozi. Mirai botnet affected thousands of home routers because of weak passwords or no passwords at all, and eventually executed the largest DDOS attack ever. Even if a single device was affected by Mirai, all the other gadgets connected to that network became a part of the attacker’s C2 framework. And not only botnets, but IoT will soon become the most preferred attack surface for cybercriminals.
Attacks ranging from Ransomware, DDoS, Social-Engineering to Man-in-the-middle (MITM) will become typical if IoT security remains this way. IoT devices are dependent on apps, protocols, and various services, which give rise to insecure interfaces. Due to minimal storage capacity, IoT devices cannot employ firewalls, anti-virus, or any other security products. Each IoT device is a potential threat to the network. As the IoT device can communicate with itself, a separate encrypted network must transmit sensitive information.
The security incident where hackers gained access to a Casino’s list of filthy-rich high rollers from a thermostat attached to its smart aquarium stands as a powerful example for adopting an independent network for IoT devices. Without any doubt, IoT is one of the most innovative technological discoveries, but its continual growth and persistent connectivity are leaving it vulnerable to threat actors ready to exploit. IoT attacks will only continue to surge and threaten its users with the advancement in technology. Because being cybersecurity ready is the need of the hour it’s fundamentally critical that it be elevated as a business requirement. If your organization depends on IoT, it’s crucial to rely on a security solution that can protect your devices, data, and network from cyberattacks.

