
3 Surprising Finds in Verizon’s 2023 Data Breach Investigations Report
Verizon recently released their highly anticipated annual 2023 Data Breach Investigations Report a.k.a. DBIR. Many blog posts out there speak on the “top findings” or “top key takeaways” of the report, so I decided to focus on the things I found surprising rather than a verifcation of my suspicions.
Note: Verizon uses specific terminology that can cause confusion if misunderstood. In simple terms, ‘action variety’ means a specific type of threat action and ‘threat action’ means a general tactic employed by a threat actor. A threat action variety or action variety can come in the form of: use of stolen credentials, ransomware, phishing, pretexting, and so on.
1. Ransomware’s rise as an action variety seemingly plateaued
Over the past few years, the rapid rise of ransomware has almost been a given. Many of us are no longer surprised to hear ransomware making or breaking some nefarious record, like forcing multi-million-dollar payouts or causing multi-billion-dollar damages globally.
So, when I first saw this chart in the 2023 DBIR, which shows ransomware more-or-less holding steady as an action variety in both cyber incidents and breaches, I was surprised—at least until I realized what it actually meant.
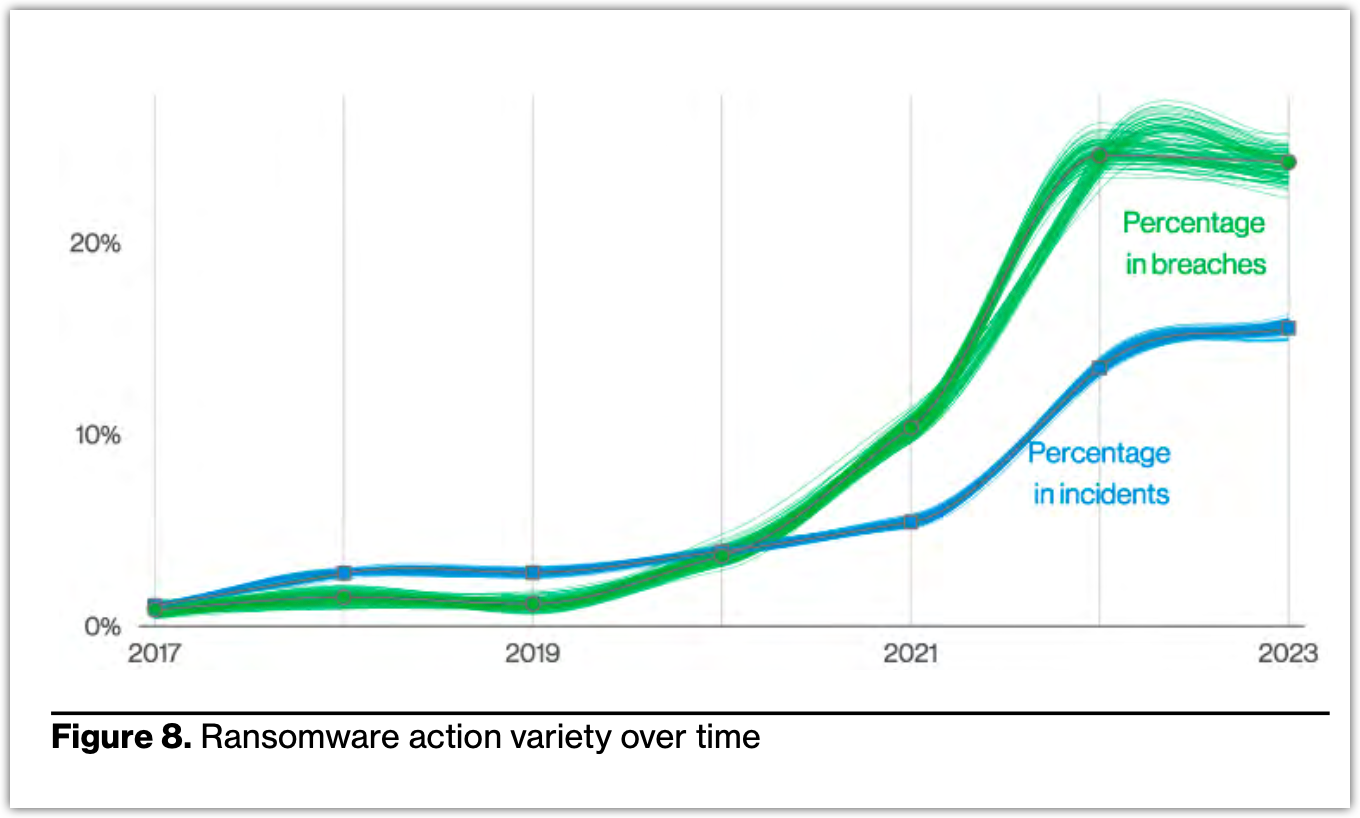
Ransomware simply can’t be incorporated into every type of incident or breach out there. For instance, it’s easy to imagine finding ransomware in incidents like system intrusions. System intrusions are attacks perpetrated by highly skilled and determined cybercriminals who employ hacking and malware deployment to breach defenses, mostly (97%) for financial gain and, in some cases (3%), for espionage.
However, it’s almost impossible to find ransomware in incidents like miscellaneous errors (e.g., misdelivery, misconfiguration, and publishing errors), Denial of Service (DoS) attacks, or even basic web application attacks.
That being said, System Intrusion-type breaches and incidents—80% of which involve ransomware—are now the top most common types of breaches and the second most common types of incidents.
Ransomware is now being detected in 24% of all recorded breaches and 15% of all incidents. To put it in another way, almost 1 out of 4 data breaches and almost 1 out of 6 security incidents involve ransomware. Those percentages have been enough to put ransomware in the number two spot as an action variety in both data breaches and security incidents (a security event that doesn’t result in unauthorized disclosure of data as in a data breach).
2. Pretexting overtakes phishing as top incident action variety
According to the report, phishing is one of three ways attackers usually gain access to an organization. If your organization has some cybersecurity program in place, chances are you know that one of the key solutions to mitigating this type of threat is security awareness training.
As part of security awareness initiatives, employees are taught how to identify phishing emails. For instance, employees are trained to spot red flags like:
- Misspelled domains, e.g., paypel.com
- Misspellings and grammatical errors
- Suspicious attachments Destination
- URLs that don’t match the link or anchor text shown in the email
- And so on
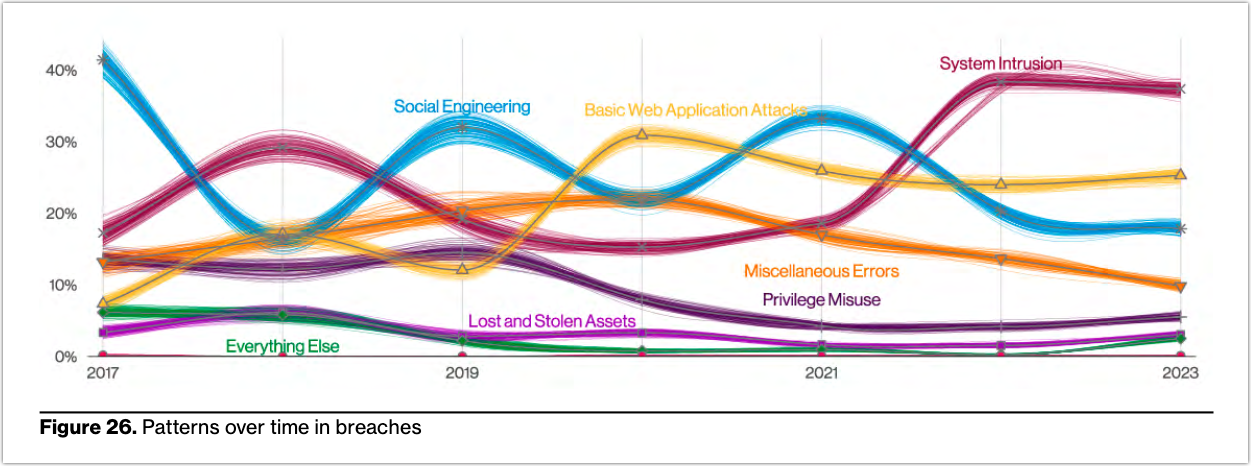
Indeed, security awareness training can be effective against phishing. There’s no question about that. However, if you review the same report, phishing is no longer the most prevalent action variety in social engineering incidents (it used to be). The top spot now belongs to pretexting.
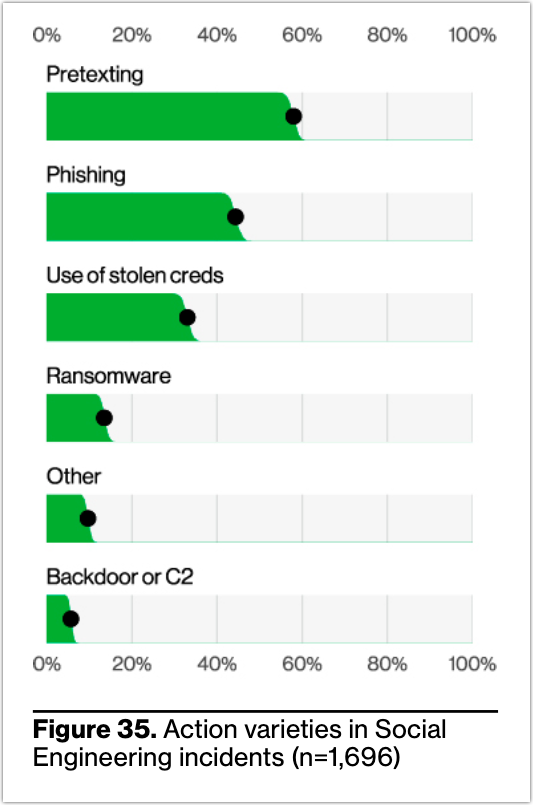
While that development alone is surprising—since phishing as an action variety has always dominated social engineering incidents—the possible implications of this development is even more startling.
This implies that security awareness training alone might just not be enough to mitigate these types of attacks. Why? Because pretexting employs social engineering techniques that are far more sophisticated and convincing than the Nigerian Prince or You-won-a-lottery types of scams.
Pretexting attackers put a lot of effort into research, planning, and execution in order to establish a pretext that resonates intimately with the intended victim. For instance, some pretexting attacks hijack existing email threads to post seemingly-legitimate requests that eventually lead to financial theft.
It’s much harder to suspect that something’s amiss if trust has already been established for a particular context—in this case, an existing email thread. What red flags are going to be triggered here? Almost none.
Recommended read: How to Stop Sophisticated Phishing Attacks
3. Manufacturing continues to climb the rankings for highest number of cyber incidents
The DBIR has this table (see screenshot of table below) that shows the number of security incidents and breaches per industry. In the latest edition of the DBIR, the Manufacturing industry is said to have recorded a total of 1,814 security incidents. That means, not counting the “Unknown” category, the Manufacturing industry has the 4th highest number of security incidents among all industries.
The Top 5 industries with the highest number of security incidents as per the 2023 DBIR are the following (see 2023 DBIR table below for reference):
- Public Administration: 3,270
- Information: 2,105
- Finance: 1,829
- Manufacturing: 1,814
- Professional: 1,396
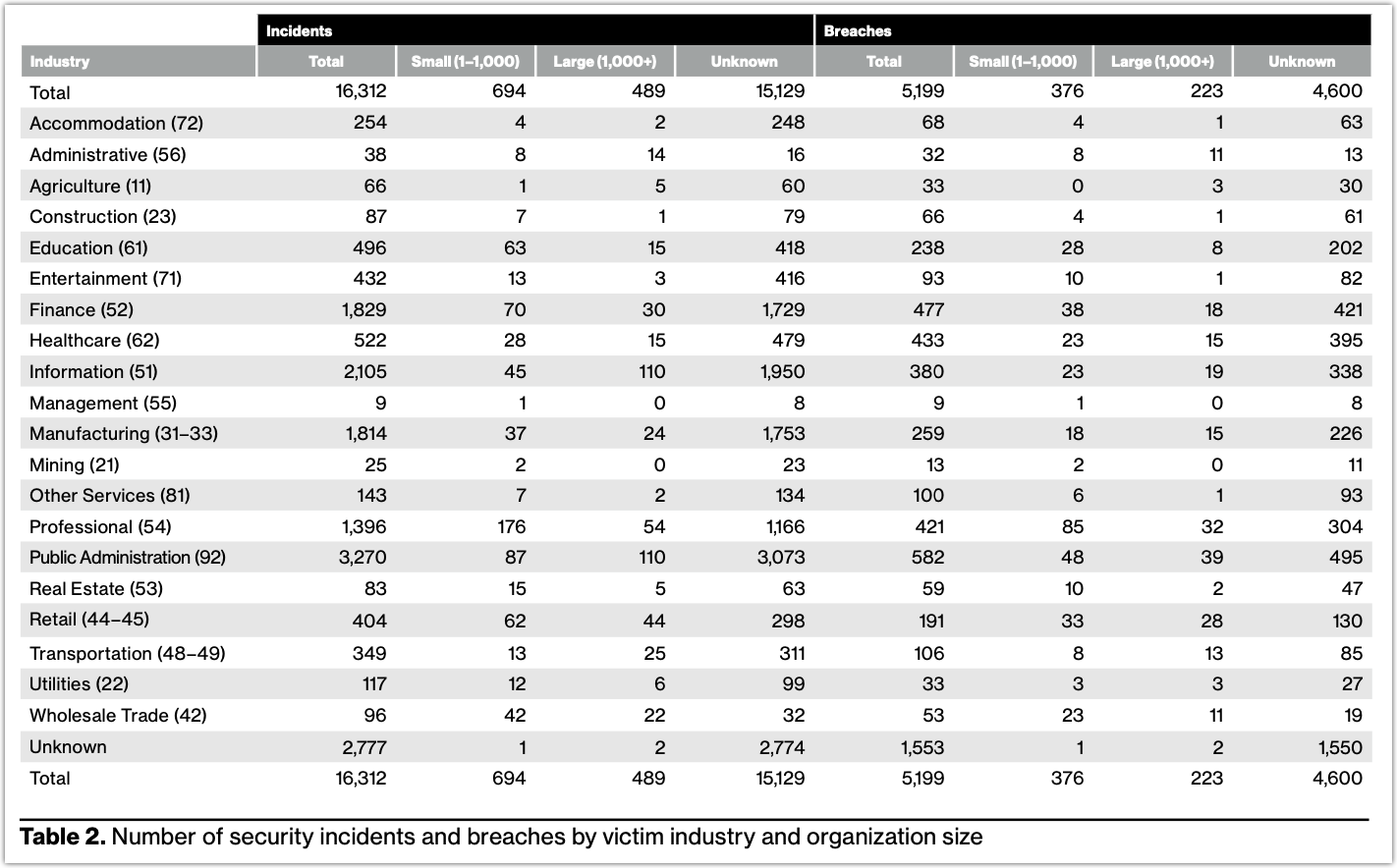
Why did I single out manufacturing? I know that manufacturing gets a substantial number of cybersecurity incidents, but I’m not sure if, compared to other industries, it’s ranked this high in that regard.
I actually tried to dig up previous editions of Verizon’s Data Breach Investigations Report, just to see where Manufacturing ranked in the previous years. This is what I discovered (see chart below).
Manufacturing ranked number 9 in the 2016 edition of the report. Its current ranking in security incident count among all industries is the highest since then. Incidents in that industry has certainly been on the rise lately.
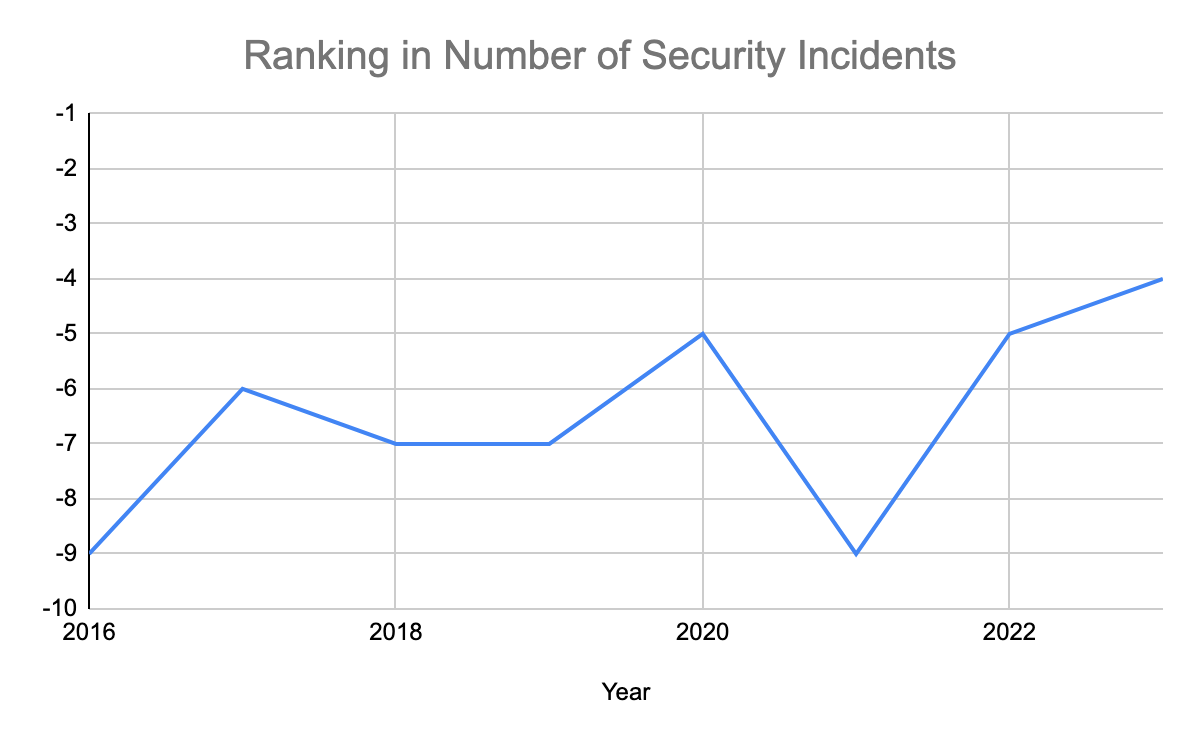
Why is this happening? There are a number of factors, but some of the key reasons why cybersecurity incidents are on the rise in manufacturing may include:
- Increased adoption of digital transformation
- Convergence of information technology (IT) and operational technology (OT)
- Rise of extortion-based threat action varieties (borrowing from DBIR terminology) like ransomware
- Widening attack surface due to adoption of technologies like cloud computing, mobile, and Industrial Internet of Things (IIoT)
For more insights, click here to access the Verizon 2023 Data Breach Investigations Report (DBIR) here.


