
APPLIED THREAT INTELLIGENCE
Expose malicious communications other solutions miss.
Your biggest security issues are the ones you don’t know about.
Start uncovering your network’s missed connections.
Missed communications are a massive security concern.
Packet sampling, traffic encryption, lack of focus on the outbound, misconfigurations, unmanaged devices. These are all common things that can cause a reduction in visibility. To fully secure something, you need to see everything that’s happening.
Know who your network is talking to.
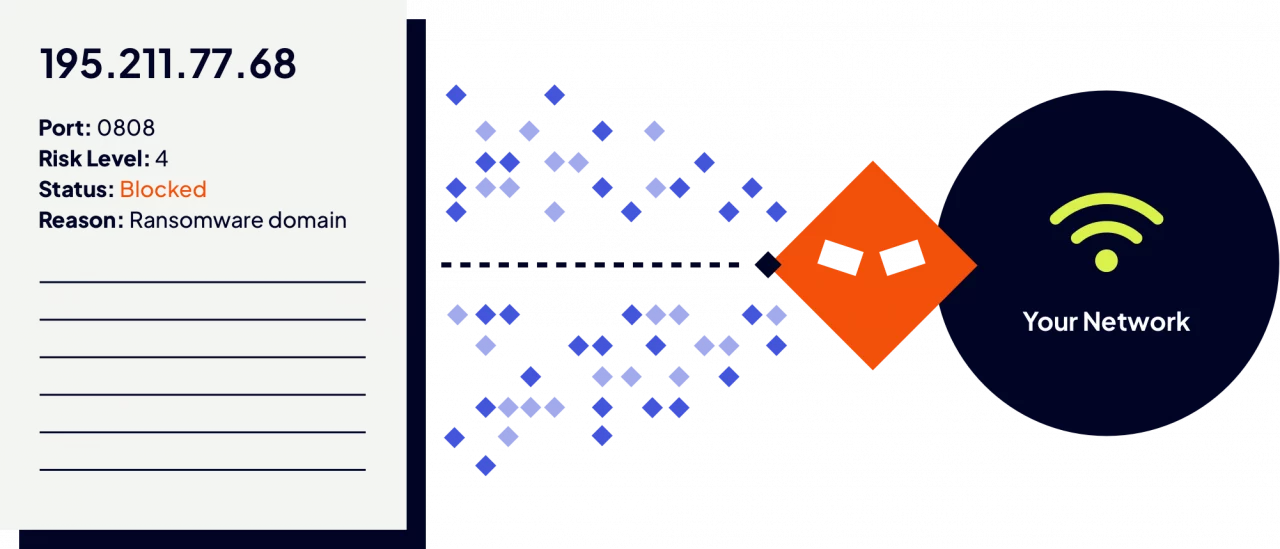
With Intrusion, you can see every connection going in and out of your network. We pair that visibility with associated threat intelligence, giving you the insights your team needs to take action on threats relevant to your business right now.

ON-PREMISE NETWORK PROTECTION
Automate on-premise security.
Monitor inbound and outbound traffic with Shield, Intrusion’s on-premise threat hunting device. Powered by our Global Threat Engine, Shield automatically identifies malicious or unknown connections.

CLOUD NETWORK SECURITY
Defend your cloud environment.
Cloud provider security is not enough. Upgrade your cloud security with Shield Cloud, a dynamic gateway between your virtual private cloud (VPC) and the public internet.

Endpoint Protection
Secure every device in your network.
Reduce risk exposure and harden your ever-expanding network surface. Shield Endpoint enables remote connectivity from any device, anywhere in the world.

THREAT HUNTING
Let our team hunt threats in your environment.
Let Intrusion help you protect your most valuable assets. We have been in the networking and threat hunting business for over 30 years. Our threat consulting team provides in-depth insights into what’s happening on your network.

